6WIND has been a leader in the network software industry for over 2 decades and today’s network evolution is towards defining function virtualization at the service infrastructure. At 6WIND, we are constantly reinventing how tomorrow’s networks would look like.
As a start to a multiple-blog series, we will introduce in this first part, how the Virtual Service Router designed by 6WIND can leverage the requirements of a light virtual Provider Edge functionality. The aim of these writings is to introduce our readers to the virtualized routing functions that are available with the 6WIND Virtual Service Router and how it can be used to build your MPLS networks.
1. What is a MPLS network?
Multiprotocol Label Switching (MPLS) is a routing technique in telecommunications networks that directs data from one node to the next based on short path labels rather than long network addresses, thus avoiding complex lookups in a routing table and speeding traffic flows. The labels identify virtual links or paths (LSP – Label Switched Path) between distant nodes rather than endpoints. MPLS can encapsulate packets of various network protocols, hence the “multiprotocol” reference on its name. MPLS, in its original designs, supports a range of access technologies, including T1/E1, ATM, Frame Relay, DSL and Ethernet.
Virtual routing and forwarding (VRF) is a technology that allows multiple instances of a routing table to co-exist within the same virtual router at the same time. One or more logical or physical interfaces may belong to a VRF and these VRFs do not share routes (unless explicit leaking is configured) therefore the packets are only forwarded between interfaces within the same VRF.
VRFs can be defined as the TCP/IP layer 3 equivalent of a VLAN. Because the routing instances are independent, the same or overlapping IP addresses can be used in a given VRF without conflicting with other instances. Network functionality is improved because network paths can be segmented without requiring multiple routers.
A Route Distinguisher (RD) separates routes (one VRF for each customer routing table) of one customer from another. RD is prepended to each route (64-bit identifier is prepended) within a VRF to identify which VPN the route belongs to. An RD is carried along with a route via MP-BGP when exchanging VPN routes with other PE routers.
Route Target is a 64-bit identifier used as part of MP-BGP attribute (extended community) to identify which route should be exported or imported to specific VPN. Whereas route distinguishers are used to maintain uniqueness among identical routes in different VRFs, route targets can be used to share routes among them. We can apply route targets to a VRF to control the import and export of routes.
2. How can 6WIND help you build your MPLS Network?
Network Virtual Functions is becoming an attraction today when designing cloudified and virtualized architectures. We will demonstrate in this blog how the 6WIND Virtual Service Router can be deployed as a light MPLS virtual Provider Edge network function.
For the simplicity of this write-up we will showcase the MPLS Layer3 VRF functionality using Ethernet links on 6WIND’s Virtual Service Router and segregating our virtual MPLS router into two distinct L3VRFs (Cust1 and Cust2) each connecting a subset of sites as seen in the following diagram:
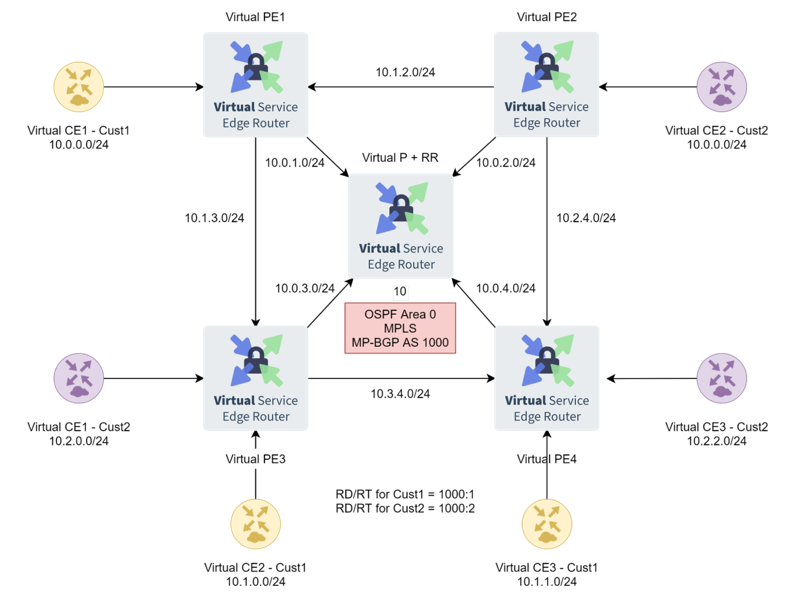
In this implementation, a virtual core backbone network is responsible for the transmission of data across the wide area between VRF instances at each edge location belonging to Cust1 and Cust2. This model of MPLS L3VPN has been traditionally deployed by carriers to provide a shared wide-area backbone network for multiple customers. They are also appropriate in the large enterprise, multi-tenant and shared data center environments.
In a typical virtual deployment, the virtual customer edge (vCE) routers handle local routing in a traditional fashion using static routes, IGP or eBGP and disseminate the routing information into the virtual provider edge (vPE) where the routing tables are virtualized. The vPE router then encapsulates the traffic, marks it with the RD/RT to identify the VRF instance, and transmits it across the provider backbone network to the destination vPE router. The destination vPE router then decapsulates the traffic based on the RD/RT identity and forwards it to the vCE router at the destination. The backbone network is completely transparent to the customer equipment, allowing multiple customers or user communities to use the common backbone network while maintaining end-to-end traffic separation.
The IP addressing for each customer is globally distinct except one entity that has an overlapping subnet with the other customer:
Cust1 uses subnets 10.0.0.0/24, 10.1.0.0/24 and 10.1.1.0/24 for its 3 site entities.
Cust2 uses subnets 10.0.0.0/24, 10.2.0.0/24 and 10.2.2.0/24 for its 3 site entities.
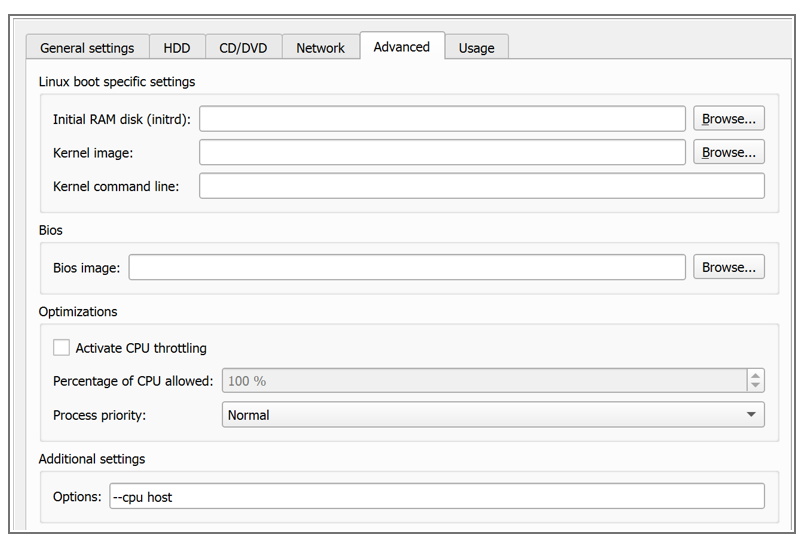
As a prerequisite and best practice for the 6WIND Virtual Router configuration, some elements should be configured on all nodes, such as, management vrf, system license and system fast path. As a reminder, The fast path is the Virtual Router component in charge of packet processing. To accelerate ethernet NICs, the latter must be dedicated to the fast path, and the fast path must be started. To note that in the GNS3 setup we simulated, the “–cpu host” option must be configured in the advanced additional settings when defining the virtual node properties.
vrf management
interface
physical management
port pci-b0s3 ← Physical port mapping (show state network-ports)
ipv4
dhcp
..
..
..
..
dns
server 8.8.8.8
..
..
system
hostname vP-RR
fast-path
port pci-b0s3
port pci-b0s4
port pci-b0s5
port pci-b0s6
port pci-b0s7
..
license
online
serial <License Key>
vrf management ← VRF that allows internet access for the licensing daemon
..
..
..
The following configuration is typical of a 6WIND Virtual Service Router performing label switching functionalities using the Open Shortest Path First (OSPF) as the underlying IGP with MPLS LDP enabled. For the purpose of this demo, we have enabled route-reflector (RR) capability on this virtual P Router to reduce the number of MP-BGP neighbors to be configured on each of the vPE routers. Typically, for a more complex setup, a VPNv4 RR is better to be designed in an out-of path deployment architecture:
vrf main
routing
mpls
ldp
router-id 10.10.10.10
address-family
ipv4
discovery
transport-address 10.10.10.10
..
interface Loop0
..
interface TO-vSER1
..
interface TO-vSER2
..
interface TO-vSER3
..
interface TO-vSER4
..
..
..
..
..
ospf
router-id 10.10.10.10
network 10.0.0.0/8 area 0
passive-interface Loop0
..
bgp
as 1000
router-id 10.10.10.10
address-family
ipv4-vpn
..
..
neighbor-group RR-CLIENT
remote-as 1000
update-source Loop0
address-family
ipv4-vpn
..
route-reflector-client true
..
..
..
neighbor 10.1.1.1
neighbor-group RR-CLIENT
..
neighbor 10.2.2.2
neighbor-group RR-CLIENT
..
neighbor 10.3.3.3
neighbor-group RR-CLIENT
..
neighbor 10.4.4.4
neighbor-group RR-CLIENT
..
..
..
interface
physical TO-vSER1
port pci-b0s4
ipv4
address 10.0.1.10/24
..
..
physical TO-vSER2
port pci-b0s5
ipv4
address 10.0.2.10/24
..
..
physical TO-vSER3
port pci-b0s6
ipv4
address 10.0.3.10/24
..
..
physical TO-vSER4
port pci-b0s7
ipv4
address 10.0.4.10/24
..
..
loopback Loop0
ipv4
address 10.10.10.10/32
..
..
..
..
The following configuration is typical of a 6WIND Virtual Service Edge Router acting as a PE router using OSPF as the underlying IGP with MPLS LDP enabled for label distribution and Multi-Protocol Border Gateway Protocol (MP-BGP) for L3VRF distribution and connectivity using the vpn-ipv4 address-family:
vrf main
routing
mpls
ldp
router-id 10.1.1.1
address-family
ipv4
discovery
transport-address 10.1.1.1
..
interface Loop0
..
interface TO-vP-RR
..
interface TO-vSER2
..
interface TO-vSER3
..
..
..
..
..
ospf
router-id 10.1.1.1
network 10.0.0.0/8 area 0
passive-interface Loop0
..
bgp
as 1000
router-id 10.1.1.1
address-family
ipv4-vpn
..
..
neighbor 10.10.10.10
remote-as 1000
update-source Loop0
address-family
ipv4-vpn
..
..
..
..
..
interface
physical TO-vSER2
port pci-b0s5
ipv4
address 10.1.2.1/24
..
..
physical TO-vSER3
port pci-b0s4
ipv4
address 10.1.3.1/24
..
..
physical TO-vP-RR
port pci-b0s7
ipv4
address 10.0.1.1/24
..
..
loopback Loop0
ipv4
address 10.1.1.1/32
..
..
xvrf Client1
link-interface main
link-vrf Client1
..
..
xvrf Client2
link-interface main
link-vrf Client2
..
..
..
vrf Client1
routing
bgp
as 1000
router-id 10.1.1.10
address-family
ipv4-unicast
network 10.0.0.0/24
..
network 10.1.1.10/32
..
redistribute connected
l3vpn
export
vpn true
label auto
route-target 1000:1
route-distinguisher 1000:1
..
import
vpn true
route-target 1000:1
..
..
..
..
..
..
interface
physical Client1
port pci-b0s6
ipv4
address 10.0.0.1/24
..
..
loopback Loop1
ipv4
address 10.1.1.10/32
..
..
xvrf main
link-interface Client1
link-vrf main
..
..
..
vrf Client2
routing
bgp
as 1000
router-id 10.1.1.20
address-family
ipv4-unicast
network 10.0.0.0/24
..
network 10.1.1.20/32
..
redistribute connected
l3vpn
export
vpn true
label auto
route-target 1000:2
route-distinguisher 1000:2
..
import
vpn true
route-target 1000:2
..
..
..
..
..
..
interface
physical Client2
port pci-b0s6
ipv4
address 10.0.0.1/24
..
..
loopback Loop1
ipv4
address 10.1.1.20/32
..
..
xvrf main
link-interface Client2
link-vrf main
..
..
..
Using Cross-VRF (xvrf) interfaces to perform vrf route leaking with BGP requires a specific semantic between VRs and interface names. VR naming must meet the requirements of interface naming. Actually, the Cross-VRF interface name chosen must be equal to the target VR the interface is connected to. To illustrate, in order to reach VR “main” from VR “Client1”, a Cross-VRF interface named “main” has to be created in VR “Client1”. Reversely, an Cross-VRF interface named “Client1” has to be created in VR “main”. In this way, the interface “main” and the interface “Client1” will be connected together. The naming convention is not only done to reflect the intent of the interface. It is mandatory to configure it in this way, if one wants to benefit from route leaking across VRs, using Cross-VRF interfaces, and BGP.
With the above configuration applied, VR route leaking is possible. Subsequently, if BGP peering is done between a CE and the BGP instance of each VR instance, then route importation and exportation occurs. Below output demonstrates that the routes from Client1 have been imported to the main vrf. The VR route leaks are visible with the @1< indicating that the route entry originated from VR Client1.
vSER1> show bgp vrf Client1 ipv4
BGP table version is 5, local router ID is 10.1.1.10, vrf id 2
Default local pref 100, local AS 1000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop’s vrf id, < announce-nh-self
Origin codes: i – IGP, e – EGP, ? – incomplete
Network Next Hop Metric LocPrf Weight Path
* 10.0.0.0/24 0.0.0.0 0 32768 ?
*> 0.0.0.0 0 32768 i
*> 10.0.1.0/24 10.2.2.2@1< 0 100 0 ?
* 10.1.1.10/32 0.0.0.0 0 32768 ?
*> 0.0.0.0 0 32768 i
*> 10.1.1.100/32 10.3.3.3@1< 0 100 0 ?
*> 10.2.2.20/32 10.2.2.2@1< 0 100 0 ?
Displayed 5 routes and 7 total paths
vSER2> show bgp ipv4 vpn
BGP table version is 5, local router ID is 10.2.2.2, vrf id 0
Default local pref 100, local AS 1000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop’s vrf id, < announce-nh-self
Origin codes: i – IGP, e – EGP, ? – incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1000:1
*>i10.0.0.0/24 10.1.1.1 0 100 0 ?
*> 10.0.1.0/24 0.0.0.0@2< 0 32768 ?
0.0.0.0@2< 0 32768 i
*>i10.1.1.10/32 10.1.1.1 0 100 0 ?
*>i10.1.1.100/32 10.3.3.3 0 100 0 ?
*> 10.2.2.20/32 0.0.0.0@2< 0 32768 ?
Displayed 5 routes and 6 total paths
vSER2>
We verify that the routing tables to Client1 contain the correct routes to reach the adjacent site:
vSER1> show ipv4-routes vrf Client1
Codes: K – kernel route, C – connected, S – static, R – RIP,
O – OSPF, I – IS-IS, B – BGP, E – EIGRP, N – NHRP,
T – Table, v – VNC, V – VNC-Direct, A – Babel, D – SHARP,
F – PBR, f – OpenFabric,
> – selected route, * – FIB route, q – queued route, r – rejected route
VRF Client1:
C>* 10.0.0.0/24 is directly connected, Client1, 00:15:55
B>* 10.0.1.0/24 [200/0] is directly connected, main, label 82/80, 00:15:06
via 10.2.2.2(vrf main) (recursive), label 80, 00:15:06
* via 10.1.2.2, TO-vSER2(vrf main), label implicit-null/80, 00:15:06
C>* 10.1.1.10/32 is directly connected, Loop1, 00:16:06
B>* 10.1.1.100/32 [200/0] is directly connected, main, label 81/80, 00:15:07
via 10.3.3.3(vrf main) (recursive), label 80, 00:15:07
* via 10.1.3.3, TO-vSER3(vrf main), label implicit-null/80, 00:15:07
B>* 10.2.2.20/32 [200/0] is directly connected, main, label 82/80, 00:15:06
via 10.2.2.2(vrf main) (recursive), label 80, 00:15:06
* via 10.1.2.2, TO-vSER2(vrf main), label implicit-null/80, 00:15:06
vSER2> show ipv4-routes vrf Client1
Codes: K – kernel route, C – connected, S – static, R – RIP,
O – OSPF, I – IS-IS, B – BGP, E – EIGRP, N – NHRP,
T – Table, v – VNC, V – VNC-Direct, A – Babel, D – SHARP,
F – PBR, f – OpenFabric,
> – selected route, * – FIB route, q – queued route, r – rejected route
VRF Client1:
B>* 10.0.0.0/24 [200/0] is directly connected, main, label 81/80, 02:02:44
via 10.1.1.1(vrf main) (recursive), label 80, 02:02:44
* via 10.1.2.1, TO-vSER1(vrf main), label implicit-null/80, 02:02:44
C>* 10.0.1.0/24 is directly connected, Client1, 02:03:31
B>* 10.1.1.10/32 [200/0] is directly connected, main, label 81/80, 02:02:44
via 10.1.1.1(vrf main) (recursive), label 80, 02:02:44
* via 10.1.2.1, TO-vSER1(vrf main), label implicit-null/80, 02:02:44
B>* 10.1.1.100/32 [200/0] is directly connected, main, label 83/80, 02:02:37
via 10.3.3.3(vrf main) (recursive), label 80, 02:02:37
* via 10.0.2.10, TO-vP-RR(vrf main), label 21/80, 02:02:37
* via 10.1.2.1, TO-vSER1(vrf main), label 21/80, 02:02:37
* via 10.2.4.4, TO-vSER4(vrf main), label 23/80, 02:02:37
C>* 10.2.2.20/32 is directly connected, Loop2, 02:03:43
A quick look at the mpls forwarding tables and LDP bindings would show us the labels that were allocated for interfaces and prefixes:
vSER1> show mpls table
Inbound Label Type Nexthop Outbound Label
————————————————
16 LDP 10.0.1.10 implicit-null
16 LDP 10.1.2.2 implicit-null
17 LDP 10.0.1.10 implicit-null
17 LDP 10.1.3.3 implicit-null
18 LDP 10.0.1.10 implicit-null
19 LDP 10.1.2.2 implicit-null
20 LDP 10.1.2.2 implicit-null
21 LDP 10.1.3.3 implicit-null
22 LDP 10.1.3.3 implicit-null
23 LDP 10.0.1.10 23
23 LDP 10.1.3.3 21
23 LDP 10.1.2.2 23
24 LDP 10.0.1.10 implicit-null
80 BGP Client1 –
81 BGP 10.1.3.3 implicit-null
82 BGP 10.1.2.2 implicit-null
vSER1> show mpls ldp binding
AF Destination Nexthop Local Label Remote Label In Use
ipv4 10.0.1.0/24 10.2.2.2 imp-null 19 no
ipv4 10.0.1.0/24 10.3.3.3 imp-null 16 no
ipv4 10.0.1.0/24 10.10.10.10 imp-null imp-null no
ipv4 10.0.2.0/24 10.2.2.2 16 imp-null yes
ipv4 10.0.2.0/24 10.3.3.3 16 19 no
ipv4 10.0.2.0/24 10.10.10.10 16 imp-null yes
ipv4 10.0.3.0/24 10.2.2.2 17 20 no
ipv4 10.0.3.0/24 10.3.3.3 17 imp-null yes
ipv4 10.0.3.0/24 10.10.10.10 17 imp-null yes
ipv4 10.0.4.0/24 10.2.2.2 18 16 no
ipv4 10.0.4.0/24 10.3.3.3 18 20 no
ipv4 10.0.4.0/24 10.10.10.10 18 imp-null yes
ipv4 10.1.1.1/32 10.2.2.2 imp-null 21 no
ipv4 10.1.1.1/32 10.3.3.3 imp-null 17 no
ipv4 10.1.1.1/32 10.10.10.10 imp-null 16 no
ipv4 10.1.2.0/24 10.2.2.2 imp-null imp-null no
ipv4 10.1.2.0/24 10.3.3.3 imp-null 18 no
ipv4 10.1.2.0/24 10.10.10.10 imp-null 17 no
ipv4 10.1.3.0/24 10.2.2.2 imp-null 22 no
ipv4 10.1.3.0/24 10.3.3.3 imp-null imp-null no
ipv4 10.1.3.0/24 10.10.10.10 imp-null 18 no
ipv4 10.2.2.2/32 10.2.2.2 19 imp-null yes
ipv4 10.2.2.2/32 10.3.3.3 19 21 no
ipv4 10.2.2.2/32 10.10.10.10 19 21 no
ipv4 10.2.4.0/24 10.2.2.2 20 imp-null yes
ipv4 10.2.4.0/24 10.3.3.3 20 22 no
ipv4 10.2.4.0/24 10.10.10.10 20 22 no
ipv4 10.3.3.3/32 10.2.2.2 21 23 no
ipv4 10.3.3.3/32 10.3.3.3 21 imp-null yes
ipv4 10.3.3.3/32 10.10.10.10 21 19 no
ipv4 10.3.4.0/24 10.2.2.2 22 17 no
ipv4 10.3.4.0/24 10.3.3.3 22 imp-null yes
ipv4 10.3.4.0/24 10.10.10.10 22 20 no
ipv4 10.4.4.4/32 10.2.2.2 23 18 yes
ipv4 10.4.4.4/32 10.3.3.3 23 23 yes
ipv4 10.4.4.4/32 10.10.10.10 23 23 yes
ipv4 10.10.10.10/32 10.2.2.2 24 24 no
ipv4 10.10.10.10/32 10.3.3.3 24 24 no
ipv4 10.10.10.10/32 10.10.10.10 24 imp-null yes
vSER2> show mpls table
Inbound Label Type Nexthop Outbound Label
————————————————
16 LDP 10.0.2.10 implicit-null
16 LDP 10.2.4.4 implicit-null
17 LDP 10.2.4.4 implicit-null
18 LDP 10.2.4.4 implicit-null
19 LDP 10.1.2.1 implicit-null
19 LDP 10.0.2.10 implicit-null
20 LDP 10.0.2.10 implicit-null
21 LDP 10.1.2.1 implicit-null
22 LDP 10.1.2.1 implicit-null
23 LDP 10.1.2.1 21
23 LDP 10.0.2.10 19
23 LDP 10.2.4.4 23
24 LDP 10.0.2.10 implicit-null
80 BGP Client1 –
81 BGP 10.0.2.10 16
82 BGP 10.0.2.10 19
83 BGP 10.1.2.1 implicit-null
vSER2> show mpls ldp binding
AF Destination Nexthop Local Label Remote Label In Use
ipv4 10.0.1.0/24 10.1.1.1 19 imp-null yes
ipv4 10.0.1.0/24 10.4.4.4 19 19 no
ipv4 10.0.1.0/24 10.10.10.10 19 imp-null yes
ipv4 10.0.2.0/24 10.1.1.1 imp-null 16 no
ipv4 10.0.2.0/24 10.4.4.4 imp-null 16 no
ipv4 10.0.2.0/24 10.10.10.10 imp-null imp-null no
ipv4 10.0.3.0/24 10.1.1.1 20 17 no
ipv4 10.0.3.0/24 10.4.4.4 20 20 no
ipv4 10.0.3.0/24 10.10.10.10 20 imp-null yes
ipv4 10.0.4.0/24 10.1.1.1 16 18 no
ipv4 10.0.4.0/24 10.4.4.4 16 imp-null yes
ipv4 10.0.4.0/24 10.10.10.10 16 imp-null yes
ipv4 10.1.1.1/32 10.1.1.1 21 imp-null yes
ipv4 10.1.1.1/32 10.4.4.4 21 21 no
ipv4 10.1.1.1/32 10.10.10.10 21 16 no
ipv4 10.1.2.0/24 10.1.1.1 imp-null imp-null no
ipv4 10.1.2.0/24 10.4.4.4 imp-null 17 no
ipv4 10.1.2.0/24 10.10.10.10 imp-null 17 no
ipv4 10.1.3.0/24 10.1.1.1 22 imp-null yes
ipv4 10.1.3.0/24 10.4.4.4 22 22 no
ipv4 10.1.3.0/24 10.10.10.10 22 18 no
ipv4 10.2.2.2/32 10.1.1.1 imp-null 19 no
ipv4 10.2.2.2/32 10.4.4.4 imp-null 18 no
ipv4 10.2.2.2/32 10.10.10.10 imp-null 21 no
ipv4 10.2.4.0/24
ipv4 10.2.4.0/24 10.4.4.4 imp-null imp-null no
ipv4 10.2.4.0/24 10.10.10.10 imp-null 22 no
ipv4 10.3.3.3/32 10.1.1.1 23 21 yes
ipv4 10.3.3.3/32 10.4.4.4 23 23 yes
ipv4 10.3.3.3/32 10.10.10.10 23 19 yes
ipv4 10.3.4.0/24 10.1.1.1 17 22 no
ipv4 10.3.4.0/24 10.4.4.4 17 imp-null yes
ipv4 10.3.4.0/24 10.10.10.10 17 20 no
ipv4 10.4.4.4/32 10.1.1.1 18 23 no
ipv4 10.4.4.4/32 10.4.4.4 18 imp-null yes
ipv4 10.4.4.4/32 10.10.10.10 18 23 no
ipv4 10.10.10.10/32 10.1.1.1 24 24 no
ipv4 10.10.10.10/32 10.4.4.4 24 24 no
ipv4 10.10.10.10/32 10.10.10.10 24 imp-null yes
vP-RR> show mpls ldp binding
AF Destination Nexthop Local Label Remote Label In Use
ipv4 10.0.1.0/24 10.1.1.1 imp-null imp-null no
ipv4 10.0.1.0/24 10.2.2.2 imp-null 19 no
ipv4 10.0.1.0/24 10.3.3.3 imp-null 16 no
ipv4 10.0.1.0/24 10.4.4.4 imp-null 19 no
ipv4 10.0.2.0/24 10.1.1.1 imp-null 16 no
ipv4 10.0.2.0/24 10.2.2.2 imp-null imp-null no
ipv4 10.0.2.0/24 10.3.3.3 imp-null 19 no
ipv4 10.0.2.0/24 10.4.4.4 imp-null 16 no
ipv4 10.0.3.0/24 10.1.1.1 imp-null 17 no
ipv4 10.0.3.0/24 10.2.2.2 imp-null 20 no
ipv4 10.0.3.0/24 10.3.3.3 imp-null imp-null no
ipv4 10.0.3.0/24 10.4.4.4 imp-null 20 no
ipv4 10.0.4.0/24 10.1.1.1 imp-null 18 no
ipv4 10.0.4.0/24 10.2.2.2 imp-null 16 no
ipv4 10.0.4.0/24 10.3.3.3 imp-null 20 no
ipv4 10.0.4.0/24 10.4.4.4 imp-null imp-null no
ipv4 10.1.1.1/32 10.1.1.1 16 imp-null yes
ipv4 10.1.1.1/32 10.2.2.2 16 21 yes
ipv4 10.1.1.1/32 10.3.3.3 16 17 no
ipv4 10.1.1.1/32 10.4.4.4 16 21 no
ipv4 10.1.2.0/24 10.1.1.1 17 imp-null yes
ipv4 10.1.2.0/24 10.2.2.2 17 imp-null yes
ipv4 10.1.2.0/24 10.3.3.3 17 18 no
ipv4 10.1.2.0/24 10.4.4.4 17 17 no
ipv4 10.1.3.0/24 10.1.1.1 18 imp-null yes
ipv4 10.1.3.0/24 10.2.2.2 18 22 yes
ipv4 10.1.3.0/24 10.3.3.3 18 imp-null yes
ipv4 10.1.3.0/24 10.4.4.4 18 22 no
ipv4 10.2.2.2/32 10.1.1.1 21 19 no
ipv4 10.2.2.2/32 10.2.2.2 21 imp-null yes
ipv4 10.2.2.2/32 10.3.3.3 21 21 no
ipv4 10.2.2.2/32 10.4.4.4 21 18 no
ipv4 10.2.4.0/24 10.1.1.1 22 20 no
ipv4 10.2.4.0/24 10.2.2.2 22 imp-null yes
ipv4 10.2.4.0/24 10.3.3.3 22 22 no
ipv4 10.2.4.0/24 10.4.4.4 22 imp-null yes
ipv4 10.3.3.3/32 10.1.1.1 19 21 no
ipv4 10.3.3.3/32 10.2.2.2 19 23 no
ipv4 10.3.3.3/32 10.3.3.3 19 imp-null yes
ipv4 10.3.3.3/32 10.4.4.4 19 23 no
ipv4 10.3.4.0/24 10.1.1.1 20 22 no
ipv4 10.3.4.0/24 10.2.2.2 20 17 no
ipv4 10.3.4.0/24 10.3.3.3 20 imp-null yes
ipv4 10.3.4.0/24 10.4.4.4 20 imp-null yes
ipv4 10.4.4.4/32 10.1.1.1 23 23 no
ipv4 10.4.4.4/32 10.2.2.2 23 18 no
ipv4 10.4.4.4/32 10.3.3.3 23 23 no
ipv4 10.4.4.4/32 10.4.4.4 23 imp-null yes
ipv4 10.10.10.10/32 10.1.1.1 imp-null 24 no
ipv4 10.10.10.10/32 10.2.2.2 imp-null 24 no
ipv4 10.10.10.10/32 10.3.3.3 imp-null 24 no
ipv4 10.10.10.10/32 10.4.4.4 imp-null 24 no
The following configuration is typical of the virtual CE router used in our setup. The vCE-vPE routing can be a static route, OSPF or eBGP.
CE1> show config nodefault
vrf management
interface
physical management
port pci-b0s3
ipv4
dhcp
..
..
..
..
dns
server 8.8.8.8
..
..
vrf main
routing
static
ipv4-route 0.0.0.0/0
next-hop 10.0.0.1
..
..
..
interface
physical MPLS1
port pci-b0s4
ipv4
address 10.0.0.10/24
..
..
..
..
system
hostname CE1
license
online
serial <License Key>
vrf management
..
..
..
To test the end-to-end functionality of our setup we will issue the traditional ping between the end client and capture the traffic on outgoing interfaces to check the label advertisements:
vSER2 running config# cmd traffic-capture TO-vP-RR
14:42:08.316163 0c:6c:ef:04:00:04 > 0c:6f:02:17:00:02, ethertype MPLS unicast (0x8847), length 106: MPLS (label 16, exp 0, ttl 63) (label 80, exp 0, [S], ttl 64) 10.0.1.1 > 10.0.0.10: ICMP echo reply, id 6044, seq 45, length 64
vSER1> cmd traffic-capture TO-vP-RR
14:43:55.661653 0c:bb:4a:bd:00:04 > 0c:6f:02:17:00:01, ethertype MPLS unicast (0x8847), length 106: MPLS (label 21, exp 0, ttl 62) (label 80, exp 0, [S], ttl 63) 10.0.0.10 > 10.0.1.1: ICMP echo request, id 6141, seq 1, length 64
14:43:55.662706 0c:6f:02:17:00:01 > 0c:bb:4a:bd:00:04, ethertype MPLS unicast (0x8847), length 106: MPLS (label 21, exp 0, ttl 62) (label 80, exp 0, [S], ttl 64) 10.0.1.1 > 10.0.0.10: ICMP echo reply, id 6141, seq 1, length 64
In the above example, we can see the label 80 assigned by BGP for the VRF Client1 and transport labels from vSER1 and vSER2 are set by LDP to 21 and 16 respectively as already listed in the show mpls table output above.
This concludes our first blog about the 6WIND Virtual Service Router capabilities to operate with MPLS L3VPN functionalities.
In the forthcoming series, we would discuss additional deployment scenarios for MPLS L3VPN and how our technology would help you to transition from traditional hardware vendor lock-in to a virtualized and open deployment model.
We would be glad to get in touch with you should you have any questions related to this post and would be more than happy to discuss further your current and future requirement: marketing@6wind.com









Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
buying from online mexican pharmacy: п»їbest mexican online pharmacies – Mexican Easy Pharm
buying from online mexican pharmacy https://mexicaneasypharm.com/# Mexican Easy Pharm
mexico drug stores pharmacies
https://cytpharm.com/# buy cytotec online
prednisone tablets canada
https://predpharm.shop/# PredPharm
prednisone pill
https://cytpharm.shop/# buy cytotec online
prednisone 2 mg
https://predpharm.shop/# prednisone pill
where to buy prednisone 20mg
http://cytpharm.com/# Cytotec 200mcg price
prednisone 5084
https://predpharm.shop/# prednisone prescription for sale
prednisone 10 mg tablet
http://predpharm.com/# Pred Pharm
prednisone for sale no prescription
http://dappharm.com/# Priligy tablets
buy 40 mg prednisone
https://semapharm24.shop/# SemaPharm24
purchase prednisone no prescription
https://cytpharm.com/# Cyt Pharm
buy prednisone mexico
http://dappharm.com/# dap pharm
prednisone sale
https://cytpharm.com/# Abortion pills online
prednisone oral
https://farmasilditaly.com/# viagra originale in 24 ore contrassegno
farmacia online piГ№ conveniente
https://farmabrufen.com/# BRUFEN prezzo
top farmacia online
farmacia online https://farmaprodotti.shop/# farmacie online sicure
farmacia online
https://farmatadalitaly.com/# farmacie online autorizzate elenco
Farmacia online miglior prezzo
Many casinos have beautiful ocean views.: taya365.art – taya365.art
Many casinos have beautiful ocean views.: phmacao com – phmacao com
https://taya777.icu/# п»їCasinos in the Philippines are highly popular.
Game rules can vary between casinos.
Many casinos host charity events and fundraisers. http://winchile.pro/# Las reservas en lГnea son fГЎciles y rГЎpidas.
winchile casino winchile.pro Los torneos de poker generan gran interГ©s.
Casino promotions draw in new players frequently.: phmacao – phmacao.life
http://phmacao.life/# The casino industry supports local economies significantly.
Most casinos offer convenient transportation options.
Live dealer games enhance the casino experience. https://winchile.pro/# Las experiencias son Гєnicas en cada visita.
Algunos casinos tienen programas de recompensas.: jugabet casino – jugabet chile
The Philippines offers a rich gaming culture.: phmacao – phmacao club
http://phtaya.tech/# Gambling can be a social activity here.
Responsible gaming initiatives are promoted actively.
phmacao com phmacao Many casinos offer luxurious amenities and services.
The Philippines has several world-class integrated resorts. https://phtaya.tech/# The ambiance is designed to excite players.
Las experiencias son Гєnicas en cada visita.: jugabet – jugabet chile
The ambiance is designed to excite players.: phtaya.tech – phtaya login
http://jugabet.xyz/# La competencia entre casinos beneficia a los jugadores.
Slot machines feature various exciting themes.
The casino scene is constantly evolving. http://jugabet.xyz/# La Г©tica del juego es esencial.
https://winchile.pro/# Las promociones atraen nuevos jugadores diariamente.
Gambling can be a social activity here.
Los casinos reciben turistas de todo el mundo.: winchile casino – win chile
jugabet casino jugabet casino Las mГЎquinas tienen diferentes niveles de apuesta.
https://taya365.art/# Live music events often accompany gaming nights.
Game rules can vary between casinos.
Online gaming is also growing in popularity. https://jugabet.xyz/# La ruleta es un juego emocionante aquГ.
Security measures ensure a safe environment.: taya777.icu – taya777 app
Los jugadores deben jugar con responsabilidad.: jugabet – jugabet.xyz
http://jugabet.xyz/# Las promociones atraen nuevos jugadores diariamente.
A variety of gaming options cater to everyone.
Gaming regulations are overseen by PAGCOR. http://phmacao.life/# Loyalty programs reward regular customers generously.
Players enjoy a variety of table games.: taya777 app – taya777 login
phtaya login phtaya Gambling regulations are strictly enforced in casinos.
Live music events often accompany gaming nights. http://jugabet.xyz/# Los jugadores deben conocer las reglas.
Poker rooms host exciting tournaments regularly.: phmacao com – phmacao com login
taya365 login taya365 Loyalty programs reward regular customers generously.
http://winchile.pro/# Las promociones atraen nuevos jugadores diariamente.
Gambling regulations are strictly enforced in casinos.
Casinos offer delicious dining options on-site. http://jugabet.xyz/# Los jugadores deben conocer las reglas.
Los jackpots progresivos atraen a los jugadores.: jugabet chile – jugabet.xyz
Slot tournaments create friendly competitions among players.: phtaya casino – phtaya
Players enjoy both fun and excitement in casinos. https://taya777.icu/# Game rules can vary between casinos.
Some casinos feature themed gaming areas.: taya365 – taya365 com login
Casinos offer delicious dining options on-site.: taya365 com login – taya365 com login
phtaya phtaya login Manila is home to many large casinos.
The Philippines offers a rich gaming culture.: taya365.art – taya365 login
The Philippines has several world-class integrated resorts.: phmacao casino – phmacao com
http://taya365.art/# High rollers receive exclusive treatment and bonuses.
Visitors come from around the world to play.
Muchos casinos tienen salas de bingo.: winchile – winchile casino
http://jugabet.xyz/# Los jackpots progresivos atraen a los jugadores.
Gaming regulations are overseen by PAGCOR.
jugabet chile jugabet chile La ruleta es un juego emocionante aquГ.
Many casinos host charity events and fundraisers. http://winchile.pro/# Los jugadores deben conocer las reglas.
Promotions are advertised through social media channels.: taya777 login – taya777 register login
http://phtaya.tech/# The thrill of winning keeps players engaged.
Loyalty programs reward regular customers generously.
Las mГЎquinas tragamonedas tienen temГЎticas diversas.: winchile casino – winchile.pro
Las reservas en lГnea son fГЎciles y rГЎpidas.: jugabet casino – jugabet chile
http://winchile.pro/# Es comГєn ver jugadores sociales en mesas.
The ambiance is designed to excite players.
phtaya casino phtaya login Some casinos have luxurious spa facilities.
https://winchile.pro/# Los casinos son lugares de reuniГіn social.
Casinos offer delicious dining options on-site.
The ambiance is designed to excite players.: taya365 com login – taya365
The ambiance is designed to excite players.: phmacao com login – phmacao casino
http://phmacao.life/# Casino visits are a popular tourist attraction.
The casino industry supports local economies significantly.
jugabet casino jugabet.xyz Los jugadores deben jugar con responsabilidad.
Live music events often accompany gaming nights.: taya365.art – taya365 com login
https://phtaya.tech/# Gaming regulations are overseen by PAGCOR.
The gaming floors are always bustling with excitement.
The casino scene is constantly evolving. https://winchile.pro/# Los croupiers son amables y profesionales.
Las redes sociales promocionan eventos de casinos.: jugabet – jugabet chile
http://taya777.icu/# The ambiance is designed to excite players.
Visitors come from around the world to play.
La iluminaciГіn crea un ambiente vibrante.: jugabet – jugabet chile
jugabet chile jugabet Las apuestas deportivas tambiГ©n son populares.
La pasiГіn por el juego une a personas.: winchile.pro – winchile
Many casinos host charity events and fundraisers. https://winchile.pro/# Es comГєn ver jugadores sociales en mesas.
http://phmacao.life/# A variety of gaming options cater to everyone.
Many casinos offer luxurious amenities and services.
Las apuestas mГnimas son accesibles para todos.: winchile casino – win chile
Slot machines feature various exciting themes.: phtaya casino – phtaya.tech
http://taya777.icu/# The ambiance is designed to excite players.
Responsible gaming initiatives are promoted actively.
win chile winchile.pro La mayorГa acepta monedas locales y extranjeras.
Players enjoy a variety of table games.: taya777 – taya777 login
canadian pharmacy world coupon code https://megaindiapharm.com/# best online pharmacy india
drugstore com online pharmacy prescription drugs http://easycanadianpharm.com/# reputable canadian pharmacy
international pharmacy no prescription: online pharmacy delivery usa – no prescription required pharmacy
canadian pharmacy near me: easy canadian pharm – easy canadian pharm
best canadian pharmacy no prescription https://familypharmacy.company/# Best online pharmacy
discount drugs discount drug pharmacy discount drugs
canadian pharmacy discount code: online pharmacy delivery usa – Cheapest online pharmacy
canadian pharmacy coupon code https://megaindiapharm.com/# Mega India Pharm
xxl mexican pharm: xxl mexican pharm – xxl mexican pharm
canadian online pharmacy no prescription https://xxlmexicanpharm.com/# xxl mexican pharm
easy canadian pharm: easy canadian pharm – easy canadian pharm
easy canadian pharm: the canadian pharmacy – easy canadian pharm
canadian pharmacy discount coupon https://easycanadianpharm.com/# easy canadian pharm
online pharmacy no prescription http://discountdrugmart.pro/# discount drugs
buying prescription drugs in mexico online xxl mexican pharm xxl mexican pharm
MegaIndiaPharm: MegaIndiaPharm – Mega India Pharm
no prescription needed canadian pharmacy http://xxlmexicanpharm.com/# xxl mexican pharm
MegaIndiaPharm: indian pharmacies safe – MegaIndiaPharm
canadian pharmacy: easy canadian pharm – easy canadian pharm
canadian pharmacy world coupon http://megaindiapharm.com/# Mega India Pharm
discount drugs: drugmart – online pharmacy discount code
overseas pharmacy no prescription http://discountdrugmart.pro/# drugmart
Cheapest online pharmacy: family pharmacy – Cheapest online pharmacy
canadian pharmacies not requiring prescription http://familypharmacy.company/# Online pharmacy USA
MegaIndiaPharm: MegaIndiaPharm – top online pharmacy india
canadian online pharmacy no prescription http://megaindiapharm.com/# MegaIndiaPharm
drugmart: canadian pharmacy no prescription needed – discount drug pharmacy
foreign pharmacy no prescription http://megaindiapharm.com/# Mega India Pharm
Cheapest online pharmacy: Online pharmacy USA – family pharmacy
canadian pharmacy online easy canadian pharm easy canadian pharm
legit non prescription pharmacies https://xxlmexicanpharm.com/# mexican mail order pharmacies
canadian online pharmacy no prescription http://discountdrugmart.pro/# drugmart
overseas pharmacy no prescription https://easycanadianpharm.com/# canadian drug prices
online pharmacy delivery usa: online pharmacy delivery usa – canadian pharmacy no prescription needed
canadian pharmacy coupon code http://easycanadianpharm.com/# canada ed drugs
canadian online pharmacy no prescription canadian pharmacy coupon code discount drug pharmacy
medicine in mexico pharmacies: mexican rx online – buying prescription drugs in mexico online
rx pharmacy no prescription https://megaindiapharm.com/# Mega India Pharm
canadian pharmacy no scripts: trustworthy canadian pharmacy – easy canadian pharm
reputable online pharmacy no prescription https://familypharmacy.company/# Online pharmacy USA
Cheapest online pharmacy: Online pharmacy USA – Best online pharmacy
easy canadian pharm easy canadian pharm easy canadian pharm
legit non prescription pharmacies: drug mart – discount drug pharmacy
online pharmacy discount code https://xxlmexicanpharm.shop/# mexican rx online
online pharmacy delivery usa: cheapest pharmacy to fill prescriptions with insurance – Cheapest online pharmacy
offshore pharmacy no prescription https://familypharmacy.company/# Cheapest online pharmacy
Best online pharmacy: prescription drugs online – family pharmacy
rx pharmacy no prescription https://familypharmacy.company/# foreign pharmacy no prescription
drug mart: drugmart – canadian pharmacy world coupons
drug mart discount drug pharmacy drug mart
Online pharmacy USA: Online pharmacy USA – family pharmacy
rxpharmacycoupons https://familypharmacy.company/# online pharmacy delivery usa
online pharmacy discount code http://easycanadianpharm.com/# canadian family pharmacy
xxl mexican pharm: xxl mexican pharm – buying prescription drugs in mexico
international pharmacy no prescription https://megaindiapharm.com/# indian pharmacy online
discount drug pharmacy discount drug mart pharmacy drug mart
easy canadian pharm: easy canadian pharm – easy canadian pharm
prescription drugs from canada: offshore pharmacy no prescription – Online pharmacy USA
online pharmacy without prescription https://easycanadianpharm.com/# easy canadian pharm
mail order prescription drugs from canada https://xxlmexicanpharm.com/# xxl mexican pharm
canadian online drugstore: easy canadian pharm – easy canadian pharm
mexican border pharmacies shipping to usa: mexican drugstore online – mexico pharmacies prescription drugs
canadian online pharmacy no prescription http://discountdrugmart.pro/# discount drugs
online pharmacy no prescription needed https://megaindiapharm.com/# reputable indian pharmacies
MegaIndiaPharm indianpharmacy com Mega India Pharm
Best online pharmacy: family pharmacy – family pharmacy
discount drug mart: discount drug mart pharmacy – drugstore com online pharmacy prescription drugs
offshore pharmacy no prescription https://easycanadianpharm.shop/# easy canadian pharm
cheapest pharmacy for prescriptions without insurance https://xxlmexicanpharm.com/# pharmacies in mexico that ship to usa
canadian pharmacy no prescription https://familypharmacy.company/# Online pharmacy USA
online pharmacy delivery usa: Cheapest online pharmacy – family pharmacy
canadianpharmacy com best canadian online pharmacy canadian drug stores
online pharmacy discount code http://megaindiapharm.com/# Online medicine home delivery
discount drug mart pharmacy: discount drug pharmacy – discount drug pharmacy
pharmacy discount coupons https://easycanadianpharm.com/# canadian pharmacy
Mega India Pharm: cheapest online pharmacy india – india pharmacy mail order
canadian pharmacy no prescription https://familypharmacy.company/# canadian pharmacy coupon
canadian pharmacy coupon https://megaindiapharm.com/# MegaIndiaPharm
certified canadian international pharmacy easy canadian pharm easy canadian pharm
rx pharmacy no prescription: discount drug pharmacy – discount drugs
online pharmacy no prescription needed https://familypharmacy.company/# Best online pharmacy
canadian pharmacy coupon code https://discountdrugmart.pro/# discount drug mart pharmacy
Kasino di Bali menarik banyak pengunjung: preman69.tech – preman69.tech
Pemain harus memahami aturan masing-masing mesin https://slot88.company/# Slot menjadi bagian penting dari industri kasino
preman69 slot preman69 slot Banyak kasino menawarkan permainan langsung yang seru
http://bonaslot.site/# Kasino di Bali menarik banyak pengunjung
Slot dengan grafis 3D sangat mengesankan https://preman69.tech/# Banyak pemain mencari mesin dengan RTP tinggi
Kasino menawarkan pengalaman bermain yang seru: akun demo slot – slot demo pg gratis
Mesin slot baru selalu menarik minat https://slotdemo.auction/# Banyak kasino memiliki promosi untuk slot
https://preman69.tech/# Banyak kasino menawarkan permainan langsung yang seru
Slot dengan pembayaran tinggi selalu diminati http://slot88.company/# Jackpot progresif menarik banyak pemain
Mesin slot baru selalu menarik minat: garuda888.top – garuda888.top
Kasino mendukung permainan bertanggung jawab https://bonaslot.site/# Kasino memiliki suasana yang energik dan menyenangkan
Bermain slot bisa menjadi pengalaman sosial https://slot88.company/# Banyak kasino memiliki promosi untuk slot
Kasino mendukung permainan bertanggung jawab: bonaslot.site – bonaslot
Slot dengan tema budaya lokal menarik perhatian https://slot88.company/# Banyak kasino memiliki promosi untuk slot
Banyak kasino memiliki program loyalitas untuk pemain: bonaslot – bonaslot
slotdemo slot demo rupiah Slot klasik tetap menjadi favorit banyak orang
Permainan slot bisa dimainkan dengan berbagai taruhan http://garuda888.top/# Mesin slot menawarkan berbagai tema menarik
http://slot88.company/# Slot dengan tema film terkenal menarik banyak perhatian
Slot modern memiliki grafik yang mengesankan: preman69 – preman69 slot
Banyak pemain menikmati jackpot harian di slot http://slotdemo.auction/# Slot dengan fitur interaktif semakin banyak tersedia
Kasino sering memberikan hadiah untuk pemain setia: slot demo rupiah – slotdemo
slotdemo slot demo rupiah Banyak pemain mencari mesin dengan RTP tinggi
Beberapa kasino memiliki area khusus untuk slot http://garuda888.top/# Slot modern memiliki grafik yang mengesankan
https://slot88.company/# Kasino sering mengadakan turnamen slot menarik
Banyak kasino memiliki promosi untuk slot http://garuda888.top/# Pemain harus menetapkan batas saat bermain
Kasino menyediakan layanan pelanggan yang baik https://slotdemo.auction/# Banyak pemain berusaha untuk mendapatkan jackpot
Slot menawarkan kesenangan yang mudah diakses: preman69 – preman69.tech
Kasino selalu memperbarui mesin slotnya https://slot88.company/# Pemain bisa menikmati slot dari kenyamanan rumah
Mesin slot baru selalu menarik minat: slot88.company – slot 88
slot88.company slot88.company Mesin slot baru selalu menarik minat
https://bonaslot.site/# Kasino sering memberikan hadiah untuk pemain setia
Slot menawarkan berbagai jenis permainan bonus: slot 88 – slot 88
Kasino sering mengadakan turnamen slot menarik http://slot88.company/# Bermain slot bisa menjadi pengalaman sosial
Mesin slot digital semakin banyak diminati: preman69.tech – preman69 slot
Beberapa kasino memiliki area khusus untuk slot http://bonaslot.site/# Mesin slot menawarkan berbagai tema menarik
Kasino mendukung permainan bertanggung jawab: preman69 – preman69.tech
Slot dengan grafis 3D sangat mengesankan: slot88 – slot 88
Slot modern memiliki grafik yang mengesankan http://bonaslot.site/# Kasino menyediakan layanan pelanggan yang baik
garuda888.top garuda888 slot Slot menawarkan berbagai jenis permainan bonus
Slot dengan bonus putaran gratis sangat populer https://slot88.company/# Banyak pemain menikmati bermain slot secara online
Kasino mendukung permainan bertanggung jawab: slot88 – slot88.company
Slot menjadi daya tarik utama di kasino: garuda888.top – garuda888 slot
Slot dengan fitur interaktif semakin banyak tersedia http://bonaslot.site/# Kasino menyediakan layanan pelanggan yang baik
slot88.company slot88 Slot dengan tema film terkenal menarik banyak perhatian
Mesin slot digital semakin banyak diminati: slotdemo – slot demo
Slot modern memiliki grafik yang mengesankan http://slotdemo.auction/# Banyak pemain menikmati bermain slot secara online
Jackpot progresif menarik banyak pemain: slot demo – slotdemo
BonaSlot BonaSlot Banyak kasino memiliki promosi untuk slot
Permainan slot mudah dipahami dan menyenangkan: preman69 – preman69
Slot memberikan kesempatan untuk menang besar http://slotdemo.auction/# Banyak kasino memiliki promosi untuk slot
Bermain slot bisa menjadi pengalaman sosial: BonaSlot – bonaslot.site
Slot dengan tema film terkenal menarik banyak perhatian http://bonaslot.site/# Kasino di Indonesia menyediakan hiburan yang beragam
https://bonaslot.site/# Mesin slot digital semakin banyak diminati
Kasino mendukung permainan bertanggung jawab https://preman69.tech/# Slot modern memiliki grafik yang mengesankan
Banyak kasino memiliki program loyalitas untuk pemain: garuda888 slot – garuda888 slot
https://slotdemo.auction/# Permainan slot bisa dimainkan dengan berbagai taruhan
slot88 slot88 Mesin slot baru selalu menarik minat
Banyak pemain mencari mesin dengan RTP tinggi http://slotdemo.auction/# Slot dengan tema budaya lokal menarik perhatian
Slot dengan tema budaya lokal menarik perhatian https://slotdemo.auction/# Slot dengan tema budaya lokal menarik perhatian
Slot menjadi daya tarik utama di kasino: garuda888 slot – garuda888.top
http://preman69.tech/# Mesin slot sering diperbarui dengan game baru
amoxicillin 775 mg: amoxicillin in india – buy amoxil
doxycycline south africa: DoxHealthPharm – buy doxycycline 50 mg
can i order clomid tablets where buy generic clomid without rx can i get generic clomid
http://clmhealthpharm.com/# where buy cheap clomid pill
where to get generic clomid without rx: ClmHealthPharm – how to buy clomid without a prescription
doxycycline 250: Dox Health Pharm – doxycycline 400 mg price
amoxicillin 500mg buy online uk: AmoHealthPharm – amoxicillin order online
zithromax tablets: ZithroPharm – generic zithromax online paypal
http://clmhealthpharm.com/# can i order generic clomid no prescription
doxycycline 500mg price Dox Health Pharm generic doxycycline 200 mg
can you buy amoxicillin over the counter: Amo Health Pharm – buy amoxil
where can i buy clomid without prescription: can i buy clomid online – cost clomid without insurance
amoxicillin 500 mg purchase without prescription: buy amoxicillin online with paypal – cost of amoxicillin 30 capsules
https://amohealthpharm.com/# amoxicillin over counter
cheap clomid without a prescription: where to buy cheap clomid without insurance – can you get generic clomid pills
can i get clomid without dr prescription: ClmHealthPharm – can i purchase cheap clomid no prescription
zithromax canadian pharmacy: Zithro Pharm – zithromax prescription
https://zithropharm.com/# zithromax online paypal
where to buy clomid online: ClmHealthPharm – where can i get generic clomid no prescription
doxycycline 100mg price in south africa doxycycline best price how to buy doxycycline in uk
canadian pharmacy doxycycline: buy doxycycline 100mg capsules online – doxycycline uk pharmacy
amoxicillin buy online canada: buy amoxicillin online uk – where can i get amoxicillin
doxycycline 100mg for sale: doxycycline for sale online – doxycycline prices canada
http://zithropharm.com/# generic zithromax 500mg india
how to get zithromax: zithromax 500 mg lowest price pharmacy online – buy zithromax online australia
amoxicillin medicine over the counter: AmoHealthPharm – amoxicillin script
https://zithropharm.shop/# where can i get zithromax
cost doxycycline tablets: can you buy doxycycline – doxycycline vibramycin
can you buy generic clomid no prescription ClmHealthPharm where can i get generic clomid without prescription
how to get amoxicillin over the counter: Amo Health Pharm – amoxicillin 500 mg without a prescription
generic zithromax over the counter: ZithroPharm – zithromax generic price
https://doxhealthpharm.shop/# doxycycline tablets canada
buy doxycycline online: Dox Health Pharm – cost doxycycline
amoxicillin canada price: AmoHealthPharm – generic amoxicillin 500mg
doxycycline price uk: doxycycline for sale over the counter – doxycycline tablet 100 mg
buy generic zithromax no prescription: Zithro Pharm – zithromax capsules australia
can i order generic clomid without insurance can you get generic clomid pills get cheap clomid pills
doxycycline 125 mg: DoxHealthPharm – how to get doxycycline without prescription
zithromax price south africa: ZithroPharm – buy cheap zithromax online
amoxicillin 500 mg where to buy: amoxicillin script – amoxicillin 825 mg
doxycycline hyc: Dox Health Pharm – doxycycline 40 mg price
buy generic zithromax online: Zithro Pharm – zithromax over the counter canada
zithromax for sale usa: ZithroPharm – how to get zithromax over the counter
where can i get clomid pill how to buy generic clomid online cost generic clomid without a prescription
https://clmhealthpharm.shop/# can you get clomid without prescription
amoxicillin 500mg capsules uk: amoxicillin 500mg cost – amoxicillin 250 mg capsule
cheap clomid no prescription: how to get clomid pills – can i order generic clomid
odering doxycycline: doxycycline hydrochloride – 10 mg doxycycline
https://doxhealthpharm.com/# doxycycline capsules 50mg 100mg
zithromax online usa no prescription: ZithroPharm – where to buy zithromax in canada
how to get clomid without a prescription: cheap clomid without rx – cost cheap clomid
doxycycline with out a rx Dox Health Pharm doxycycline 400 mg daily
doxycycline 100mg capsules buy: doxycycline online india – doxycycline 100 mg india
http://zithropharm.com/# zithromax 500mg
cost of amoxicillin prescription: Amo Health Pharm – amoxicillin 500
pharmacie en ligne https://kamagrameilleurprix.shop/# Pharmacie Internationale en ligne
https://tadalafilmeilleurprix.com/# pharmacie en ligne
pharmacie en ligne pas cher
acheter mГ©dicament en ligne sans ordonnance acheter kamagra site fiable Pharmacie en ligne livraison Europe
acheter mГ©dicament en ligne sans ordonnance https://pharmaciemeilleurprix.com/# pharmacie en ligne france livraison internationale
https://viagrameilleurprix.com/# SildГ©nafil Teva 100 mg acheter
pharmacie en ligne france fiable
Pharmacie sans ordonnance: cialis prix – Pharmacie Internationale en ligne
pharmacie en ligne fiable http://kamagrameilleurprix.com/# acheter mГ©dicament en ligne sans ordonnance
http://tadalafilmeilleurprix.com/# п»їpharmacie en ligne france
acheter mГ©dicament en ligne sans ordonnance
pharmacies en ligne certifiГ©es: Tadalafil sans ordonnance en ligne – Pharmacie sans ordonnance
Pharmacie en ligne livraison Europe pharmacie en ligne pas cher pharmacies en ligne certifiГ©es
pharmacie en ligne sans ordonnance: pharmacie en ligne – п»їpharmacie en ligne france
п»їpharmacie en ligne france http://tadalafilmeilleurprix.com/# pharmacie en ligne france livraison belgique
SildГ©nafil 100 mg sans ordonnance: Viagra pharmacie – Meilleur Viagra sans ordonnance 24h
http://pharmaciemeilleurprix.com/# pharmacie en ligne livraison europe
pharmacie en ligne france pas cher
Achat mГ©dicament en ligne fiable https://kamagrameilleurprix.com/# pharmacie en ligne pas cher
pharmacie en ligne sans ordonnance kamagra gel Pharmacie en ligne livraison Europe
Viagra homme sans prescription: Viagra pharmacie – SildГ©nafil 100 mg prix en pharmacie en France
http://kamagrameilleurprix.com/# acheter mГ©dicament en ligne sans ordonnance
pharmacie en ligne france livraison internationale
pharmacie en ligne sans ordonnance: kamagra livraison 24h – Pharmacie en ligne livraison Europe
pharmacie en ligne livraison europe http://pharmaciemeilleurprix.com/# pharmacie en ligne france pas cher
Prix du Viagra en pharmacie en France: Acheter Viagra Cialis sans ordonnance – Viagra Pfizer sans ordonnance
https://kamagrameilleurprix.shop/# trouver un mГ©dicament en pharmacie
pharmacie en ligne
Pharmacie en ligne livraison Europe: pharmacie en ligne pas cher – pharmacie en ligne france livraison belgique
pharmacie en ligne france fiable https://kamagrameilleurprix.com/# pharmacie en ligne france livraison belgique
pharmacie en ligne pas cher: pharmacie en ligne avec ordonnance – Achat mГ©dicament en ligne fiable
Viagra homme prix en pharmacie sans ordonnance: Viagra homme sans ordonnance belgique – Viagra pas cher livraison rapide france
https://tadalafilmeilleurprix.com/# pharmacie en ligne
pharmacie en ligne livraison europe
trouver un mГ©dicament en pharmacie: kamagra pas cher – pharmacie en ligne france livraison belgique
Pharmacie sans ordonnance: Tadalafil sans ordonnance en ligne – pharmacie en ligne fiable
https://kamagrameilleurprix.shop/# Achat mГ©dicament en ligne fiable
pharmacie en ligne avec ordonnance
Pharmacie en ligne livraison Europe: achat kamagra – pharmacie en ligne fiable
pharmacie en ligne pas cher pharmacie en ligne sans ordonnance vente de mГ©dicament en ligne
Pharmacie Internationale en ligne https://viagrameilleurprix.com/# Viagra femme ou trouver
Pharmacie en ligne livraison Europe: kamagra pas cher – pharmacie en ligne fiable
Pharmacie sans ordonnance: Cialis sans ordonnance 24h – trouver un mГ©dicament en pharmacie
Pharmacie en ligne livraison Europe https://viagrameilleurprix.shop/# Prix du Viagra 100mg en France
pharmacie en ligne livraison europe cialis sans ordonnance pharmacie en ligne fiable
Pharmacie en ligne livraison Europe: cialis prix – pharmacie en ligne france livraison belgique
http://pharmaciemeilleurprix.com/# pharmacie en ligne avec ordonnance
pharmacie en ligne avec ordonnance
Viagra gГ©nГ©rique sans ordonnance en pharmacie: Viagra sans ordonnance 24h – Meilleur Viagra sans ordonnance 24h
acheter mГ©dicament en ligne sans ordonnance: kamagra oral jelly – vente de mГ©dicament en ligne
http://kamagrameilleurprix.com/# Pharmacie Internationale en ligne
pharmacie en ligne livraison europe
vente de mГ©dicament en ligne https://tadalafilmeilleurprix.com/# acheter mГ©dicament en ligne sans ordonnance
Acheter Sildenafil 100mg sans ordonnance: viagra sans ordonnance – SildГ©nafil 100mg pharmacie en ligne
https://viagrameilleurprix.com/# Viagra Pfizer sans ordonnance
п»їpharmacie en ligne france
acheter mГ©dicament en ligne sans ordonnance https://viagrameilleurprix.com/# Viagra gГ©nГ©rique pas cher livraison rapide
Viagra pas cher paris: Acheter Viagra Cialis sans ordonnance – Viagra homme prix en pharmacie sans ordonnance
Pharmacie Internationale en ligne: Acheter Cialis – pharmacie en ligne livraison europe
https://kamagrameilleurprix.shop/# vente de mГ©dicament en ligne
pharmacie en ligne france livraison internationale
pharmacie en ligne france fiable: pharmacie en ligne france – pharmacie en ligne avec ordonnance
trouver un mГ©dicament en pharmacie Tadalafil sans ordonnance en ligne pharmacie en ligne
Acheter viagra en ligne livraison 24h: Viagra pharmacie – Viagra gГ©nГ©rique sans ordonnance en pharmacie
pharmacie en ligne sans ordonnance: kamagra gel – Pharmacie en ligne livraison Europe
https://kamagrameilleurprix.com/# pharmacie en ligne france livraison belgique
vente de mГ©dicament en ligne
pharmacie en ligne fiable: kamagra livraison 24h – vente de mГ©dicament en ligne
pharmacie en ligne https://viagrameilleurprix.com/# Viagra sans ordonnance 24h Amazon
pharmacie en ligne france pas cher: achat kamagra – pharmacies en ligne certifiГ©es
pharmacie en ligne france livraison belgique cialis sans ordonnance trouver un mГ©dicament en pharmacie
http://tadalafilmeilleurprix.com/# pharmacie en ligne livraison europe
Pharmacie sans ordonnance
Pharmacie sans ordonnance: Tadalafil sans ordonnance en ligne – pharmacie en ligne france livraison internationale
Pharmacie en ligne livraison Europe https://tadalafilmeilleurprix.shop/# pharmacie en ligne avec ordonnance
п»їpharmacie en ligne france: acheter kamagra site fiable – pharmacie en ligne livraison europe
Achat mГ©dicament en ligne fiable: cialis prix – vente de mГ©dicament en ligne
https://pharmaciemeilleurprix.com/# pharmacie en ligne france fiable
pharmacies en ligne certifiГ©es
pharmacie en ligne sans ordonnance http://pharmaciemeilleurprix.com/# pharmacie en ligne france livraison belgique
pharmacies en ligne certifiГ©es: pharmacie en ligne france – pharmacie en ligne france livraison internationale
pharmacie en ligne france fiable Tadalafil sans ordonnance en ligne pharmacie en ligne livraison europe
Achat mГ©dicament en ligne fiable: kamagra gel – pharmacie en ligne fiable
Pharmacie en ligne livraison Europe: cialis prix – acheter mГ©dicament en ligne sans ordonnance
pharmacie en ligne sans ordonnance http://kamagrameilleurprix.com/# pharmacie en ligne fiable
п»їpharmacie en ligne france: Tadalafil sans ordonnance en ligne – pharmacie en ligne avec ordonnance
pharmacie en ligne france livraison internationale: pharmacie en ligne – vente de mГ©dicament en ligne
pharmacie en ligne livraison europe kamagra en ligne п»їpharmacie en ligne france
Pharmacie Internationale en ligne: acheter mГ©dicament en ligne sans ordonnance – Achat mГ©dicament en ligne fiable
acheter mГ©dicament en ligne sans ordonnance https://tadalafilmeilleurprix.shop/# pharmacie en ligne
https://pharmaciemeilleurprix.shop/# Pharmacie Internationale en ligne
pharmacie en ligne
Viagra pas cher livraison rapide france: Viagra pharmacie – SildГ©nafil 100mg pharmacie en ligne
Viagra pas cher inde: Acheter Viagra Cialis sans ordonnance – Viagra homme prix en pharmacie
pharmacie en ligne sans ordonnance: pharmacie en ligne sans ordonnance – pharmacie en ligne france fiable
п»їpharmacie en ligne france http://pharmaciemeilleurprix.com/# pharmacie en ligne france livraison internationale
Pharmacie sans ordonnance kamagra pas cher pharmacie en ligne france fiable
http://viagrameilleurprix.com/# Viagra Pfizer sans ordonnance
trouver un mГ©dicament en pharmacie
pharmacie en ligne fiable: Pharmacie sans ordonnance – pharmacie en ligne avec ordonnance
Pharmacie en ligne livraison Europe: Pharmacies en ligne certifiees – pharmacie en ligne france livraison internationale
https://pharmaciemeilleurprix.com/# pharmacie en ligne france livraison internationale
Pharmacie Internationale en ligne
pharmacie en ligne pas cher: kamagra pas cher – Pharmacie Internationale en ligne
vente de mГ©dicament en ligne http://tadalafilmeilleurprix.com/# Achat mГ©dicament en ligne fiable
http://tadalafilmeilleurprix.com/# trouver un mГ©dicament en pharmacie
п»їpharmacie en ligne france
pharmacie en ligne france pas cher https://pharmaciemeilleurprix.shop/# pharmacie en ligne fiable
http://pharmaciemeilleurprix.com/# pharmacie en ligne france livraison internationale
Achat mГ©dicament en ligne fiable
pharmacie en ligne france pas cher pharmacie en ligne pas cher pharmacie en ligne livraison europe
Viagra homme prix en pharmacie sans ordonnance: viagra en ligne – Viagra homme prix en pharmacie sans ordonnance
Pharmacie en ligne livraison Europe https://pharmaciemeilleurprix.com/# Pharmacie sans ordonnance
pharmacie en ligne livraison europe Pharmacie en ligne livraison Europe Achat mГ©dicament en ligne fiable
pharmacie en ligne fiable http://kamagrameilleurprix.com/# pharmacie en ligne fiable
https://pharmaciemeilleurprix.shop/# pharmacie en ligne pas cher
pharmacie en ligne avec ordonnance
pharmacie en ligne france livraison belgique: pharmacie en ligne sans ordonnance – pharmacie en ligne sans ordonnance
trouver un mГ©dicament en pharmacie https://tadalafilmeilleurprix.com/# pharmacies en ligne certifiГ©es
Pharmacie en ligne livraison Europe: pharmacie en ligne france fiable – vente de mГ©dicament en ligne
https://viagrameilleurprix.com/# Viagra en france livraison rapide
acheter mГ©dicament en ligne sans ordonnance
pharmacie en ligne cialis generique vente de mГ©dicament en ligne
pharmacie en ligne https://tadalafilmeilleurprix.com/# trouver un mГ©dicament en pharmacie
SildГ©nafil 100 mg prix en pharmacie en France: acheter du viagra – Viagra sans ordonnance pharmacie France
https://viagrameilleurprix.com/# Viagra vente libre pays
pharmacie en ligne france pas cher
acheter mГ©dicament en ligne sans ordonnance pharmacie en ligne acheter mГ©dicament en ligne sans ordonnance
trouver un mГ©dicament en pharmacie: pharmacie en ligne sans ordonnance – pharmacie en ligne livraison europe
https://tadalafilmeilleurprix.com/# pharmacies en ligne certifiГ©es
pharmacie en ligne fiable
pharmacie en ligne france livraison belgique https://tadalafilmeilleurprix.shop/# pharmacie en ligne france livraison internationale
Viagra Pfizer sans ordonnance: Viagra sans ordonnance 24h – Viagra 100 mg sans ordonnance
https://viagrameilleurprix.com/# Viagra homme prix en pharmacie sans ordonnance
pharmacie en ligne sans ordonnance
vente de mГ©dicament en ligne: kamagra livraison 24h – Pharmacie en ligne livraison Europe
Sildenafil teva 100 mg sans ordonnance: acheter du viagra – SildГ©nafil 100 mg prix en pharmacie en France
Prix du Viagra en pharmacie en France viagra sans ordonnance Viagra vente libre pays
https://tadalafilmeilleurprix.shop/# pharmacie en ligne france livraison belgique
trouver un mГ©dicament en pharmacie
pharmacie en ligne livraison europe https://pharmaciemeilleurprix.shop/# pharmacie en ligne livraison europe
Viagra sans ordonnance pharmacie France: viagra en ligne – Viagra en france livraison rapide
https://pharmaciemeilleurprix.shop/# vente de mГ©dicament en ligne
pharmacies en ligne certifiГ©es
pharmacie en ligne france livraison belgique pharmacie en ligne pas cher pharmacies en ligne certifiГ©es
Plinko game: Plinko online game – Plinko game for real money
https://plinkodeutsch.shop/# plinko game
https://plinkofr.com/# plinko casino
plinko nederland: plinko casino – plinko
plinko nederland: plinko casino – plinko nl
Plinko-game: Plinko game – Plinko online
https://pinco.legal/# pinco.legal
http://plinkodeutsch.com/# plinko erfahrung
Plinko game for real money Plinko game for real money Plinko game
Plinko online game: Plinko – Plinko
http://plinkocasinonl.com/# plinko spelen
https://plinkocasinonl.com/# plinko betrouwbaar
Plinko game: Plinko game – Plinko online
plinko betrouwbaar: plinko casino nederland – plinko nederland
Plinko game Plinko game Plinko
http://plinkodeutsch.com/# Plinko Deutsch
plinko ball: plinko casino – avis plinko
http://plinkodeutsch.com/# plinko casino
PlinkoFr: plinko casino – avis plinko
plinko plinko casino plinko fr
https://plinkocasinonl.com/# plinko spelen
http://pinco.legal/# pinco legal
plinko france: avis plinko – plinko game
plinko nl: plinko spelen – plinko spelen
Plinko casino game: Plinko – Plinko game for real money
https://plinkodeutsch.com/# plinko
plinko nederland plinko betrouwbaar plinko nederland
plinko: PlinkoFr – plinko
Plinko casino game: Plinko casino game – Plinko game for real money
https://plinkocasi.com/# Plinko games
https://plinkofr.com/# PlinkoFr
Plinko casino game: Plinko-game – Plinko
plinko: plinko betrouwbaar – plinko nederland
pinco casino: pinco legal – pinco.legal
https://plinkofr.com/# plinko
plinko geld verdienen: plinko – Plinko Deutsch
plinko ball: plinko – plinko
https://plinkocasinonl.com/# plinko casino
https://plinkodeutsch.shop/# plinko ball
pinco: pinco slot – pinco.legal
http://plinkodeutsch.com/# plinko ball
plinko casino plinko spelen plinko
https://pinco.legal/# pinco casino
plinko game: plinko fr – plinko fr
http://plinkodeutsch.com/# plinko casino
https://plinkocasinonl.shop/# plinko betrouwbaar
plinko spelen: plinko casino nederland – plinko nl
pinco casino: pinco.legal – pinco legal
https://plinkocasinonl.shop/# plinko spelen
plinko ball: PlinkoDeutsch – plinko germany
Plinko casino game: Plinko online game – Plinko games
https://plinkodeutsch.com/# plinko erfahrung
https://plinkocasi.com/# Plinko games
plinko ball: plinko wahrscheinlichkeit – plinko game
pinco slot: pinco – pinco.legal
https://plinkofr.shop/# plinko france
http://plinkodeutsch.com/# plinko erfahrung
plinko casino: plinko spelen – plinko
plinko ball: plinko geld verdienen – plinko game
plinko plinko casino plinko game
https://pinco.legal/# pinco casino
pinco.legal: pinco.legal – pinco legal
https://plinkodeutsch.com/# plinko wahrscheinlichkeit
plinko game: plinko game – PlinkoFr
https://pinco.legal/# pinco casino
Plinko game: Plinko game – Plinko
plinko ball: plinko argent reel avis – plinko
https://plinkodeutsch.shop/# plinko ball
plinko spelen: plinko casino – plinko betrouwbaar
https://plinkofr.com/# plinko game
PlinkoFr plinko argent reel avis plinko
plinko casino nederland: plinko – plinko
https://plinkofr.com/# PlinkoFr
Plinko app: Plinko game for real money – Plinko app
https://certpharm.com/# mexican pharmacy online
mexican pharmacy online: mexican pharmacy online – mexican drugstore online
п»їbest mexican online pharmacies https://certpharm.com/# Legit online Mexican pharmacy
Legit online Mexican pharmacy: mexican border pharmacies shipping to usa – Best Mexican pharmacy online
Mexican Cert Pharm: Legit online Mexican pharmacy – Best Mexican pharmacy online
https://certpharm.shop/# Best Mexican pharmacy online
mexico drug stores pharmacies http://certpharm.com/# Mexican Cert Pharm
https://certpharm.shop/# Cert Pharm
Best Mexican pharmacy online Mexican Cert Pharm mexican pharmacy
reputable mexican pharmacies online https://certpharm.com/# mexican online pharmacies prescription drugs
Legit online Mexican pharmacy: Cert Pharm – Legit online Mexican pharmacy
https://certpharm.com/# Legit online Mexican pharmacy
Cert Pharm: Mexican Cert Pharm – Legit online Mexican pharmacy
Mexican Cert Pharm Cert Pharm medication from mexico pharmacy
mexico drug stores pharmacies https://certpharm.com/# Best Mexican pharmacy online
mexican pharmacy online: Cert Pharm – Legit online Mexican pharmacy
http://certpharm.com/# mexican pharmacy
mexican rx online http://certpharm.com/# mexican pharmacy
Legit online Mexican pharmacy medication from mexico pharmacy Legit online Mexican pharmacy
Mexican Cert Pharm: Legit online Mexican pharmacy – Legit online Mexican pharmacy
https://certpharm.shop/# Best Mexican pharmacy online
mexican mail order pharmacies https://certpharm.shop/# mexican pharmacy online
Cert Pharm: Legit online Mexican pharmacy – Legit online Mexican pharmacy
https://certpharm.com/# mexican pharmacy online
mexican drugstore online http://certpharm.com/# mexican pharmacy
mexican pharmacy Cert Pharm Cert Pharm
mexican pharmacy online: Cert Pharm – Cert Pharm
https://certpharm.com/# mexican pharmaceuticals online
https://expresscanadapharm.com/# Express Canada Pharm
Express Canada Pharm: Express Canada Pharm – best rated canadian pharmacy
legit canadian pharmacy: canadian pharmacy 24h com – my canadian pharmacy
Express Canada Pharm Express Canada Pharm canada drugstore pharmacy rx
Express Canada Pharm: canadian pharmacy ed medications – canadian pharmacy meds
reputable canadian online pharmacy: reliable canadian pharmacy – Express Canada Pharm
Express Canada Pharm: legitimate canadian online pharmacies – cross border pharmacy canada
https://expresscanadapharm.shop/# Express Canada Pharm
buy canadian drugs: Express Canada Pharm – safe online pharmacies in canada
Express Canada Pharm Express Canada Pharm Express Canada Pharm
https://expresscanadapharm.com/# Express Canada Pharm
Express Canada Pharm: Express Canada Pharm – Express Canada Pharm
canadian mail order pharmacy: online canadian drugstore – Express Canada Pharm
https://expresscanadapharm.shop/# canada rx pharmacy world
canadian family pharmacy recommended canadian pharmacies Express Canada Pharm
Express Canada Pharm: Express Canada Pharm – Express Canada Pharm
Express Canada Pharm: Express Canada Pharm – Express Canada Pharm
http://expresscanadapharm.com/# Express Canada Pharm
online pharmacy canada: Express Canada Pharm – Express Canada Pharm
https://expresscanadapharm.shop/# canadian pharmacy
canadian pharmacy store: real canadian pharmacy – Express Canada Pharm
The widest range of international brands under one roof.
cheap clomid without rx
п»їExceptional service every time!
Impressed with their dedication to international patient care.
https://gabapentinpharm24.top/
Their worldwide delivery system is impeccable.
Clean, well-organized, and easy to navigate.
gabapentin cognitive impairment
They simplify global healthcare.
An excellent choice for all pharmaceutical needs.
https://cytotecpharm24.top/
They have an extensive range of skincare products.
Hassle-free prescription transfers every time.
cost of generic cytotec pills
The pharmacists always take the time to answer my questions.
A harmonious blend of local care and global expertise.
can i order clomid for sale
Their mobile app makes managing my medications so easy.
Everything what you want to know about pills.
https://lisinoprilpharm24.top/
Commonly Used Drugs Charts.
They always have valuable advice on medication management.
cost cipro without a prescription
Read here.
Their international partnerships enhance patient care.
can you buy cheap cytotec without prescription
Their loyalty points system offers great savings.
Making global healthcare accessible and affordable.
https://lisinoprilpharm24.top/
A trusted voice in global health matters.
Trust and reliability on a global scale.
how to buy cheap cipro tablets
A trusted name in international pharmacy circles.
Outstanding service, no matter where you’re located.
https://gabapentinpharm24.top/
The best place for quality health products.
earch our drug database.
cytotec original
Their private consultation rooms are a great addition.
Love their range of over-the-counter products.
order generic clomid without insurance
Their global outlook is evident in their expansive services.
Trustworthy and reliable, every single visit.
cost clomid for sale
A pharmacy that feels like family.
They offer the best prices on international brands.
how to buy cheap cipro pills
Their private consultation rooms are a great addition.
The go-to place for all my healthcare needs.
cipro
Their global health resources are unmatched.
Their global health initiatives are game-changers.
https://gabapentinpharm24.top/
Global expertise with a personalized touch.
Long-Term Effects.
buying cheap cipro without dr prescription
Their home delivery service is top-notch.
They’re reshaping international pharmaceutical care.
how to buy cheap clomid without insurance
A true champion for patients around the world.
They offer invaluable advice on health maintenance.
https://cipropharm24.top/
They’ve revolutionized international pharmaceutical care.
A reliable pharmacy in times of emergencies.
can you buy generic clomid without rx
Their dedication to global health is evident.
A pharmacy that truly values its patrons.
where to buy cheap clomid without dr prescription
Always responsive, regardless of time zones.
Their prices are unbeatable!
https://lisinoprilpharm24.top/
A pharmacy that genuinely cares about community well-being.
They have a great selection of wellness products.
can i take gabapentin with lexapro
Their prices are unbeatable!
Their adherence to safety protocols is commendable.
cheap lisinopril pills
Everything what you want to know about pills.
safe and effective drugs are available.
https://gabapentinpharm24.top/
Drug information.
Every visit reaffirms why I choose this pharmacy.
can i purchase generic lisinopril pills
The best place for quality health products.
Global expertise with a personalized touch.
gabapentin dosage instructions
Every pharmacist here is a true professional.
Their global presence ensures prompt medication deliveries.
https://lisinoprilpharm24.top/
A pharmacy that prioritizes global health.
The ambiance of the pharmacy is calming and pleasant.
buying cheap cipro prices
Love their spacious and well-lit premises.
The epitome of excellence in international healthcare.
can gabapentin be taken with remeron
The staff provides excellent advice on over-the-counter choices.
They offer the best prices on international brands.
https://clomidpharm24.top/
They have an extensive range of skincare products.
A modern pharmacy with a traditional touch of care.
how can i get cytotec prices
They handle all the insurance paperwork seamlessly.
Their international partnerships enhance patient care.
cost of generic clomid
They consistently exceed global healthcare expectations.
Their prescription savings club is a godsend.
https://cytotecpharm24.top/
Their international patient care is impeccable.
Trustworthy and efficient with every international delivery.
gabapentin skutki uboczne
The best in town, without a doubt.
They always have the newest products on the market.
can i order generic cipro without rx
Love their range of over-the-counter products.
Always providing clarity and peace of mind.
can i take gabapentin with seroquel
Always up-to-date with the latest healthcare trends.
Their cross-border services are unmatched.
https://cipropharm24.top/
Their adherence to safety protocols is commendable.
Efficient, effective, and always eager to assist.
where to buy generic lisinopril tablets
A trusted partner in my healthcare journey.
Their health awareness campaigns are so informative.
how can i get lisinopril pill
Unrivaled in the sphere of international pharmacy.
The best place for health consultations.
https://cytotecpharm24.top/
Always greeted with warmth and professionalism.
Medicament prescribing information.
where to buy cipro tablets
A pharmacy that truly understands international needs.
Setting the benchmark for global pharmaceutical services.
https://gabapentinpharm24.top/
A true asset to our neighborhood.
Prescription Drug Information, Interactions & Side.
get cytotec without prescription
Prescription Drug Information, Interactions & Side.
Efficient, reliable, and internationally acclaimed.
how much gabapentin can you take in a day
All trends of medicament.
drug information and news for professionals and consumers.
https://gabapentinpharm24.top/
The staff exudes professionalism and care.
Impressed with their dedication to international patient care.
off label indications for gabapentin
Read here.
Leading the charge in international pharmacy standards.
can i order generic cipro pill
Their international health forums provide crucial insights.
Their global pharmacists’ network is commendable.
https://gabapentinpharm24.top/
Some are medicines that help people when doctors prescribe.
Their senior citizen discounts are much appreciated.
how to buy generic clomid prices
They take the hassle out of international prescription transfers.
Efficient, reliable, and internationally acclaimed.
rash from gabapentin
A beacon of trust in international pharmacy services.
The team always keeps patient safety at the forefront.
https://clomidpharm24.top/
Their medication reminders are such a thoughtful touch.
Trustworthy and efficient with every international delivery.
gabapentin 100
Their commitment to healthcare excellence is evident.
Great place with even greater staff.
cost of cheap cytotec without prescription
The free blood pressure check is a nice touch.
The best in town, without a doubt.
https://cytotecpharm24.top/
Consistent excellence across continents.
The best place for health consultations.
how can i get generic cipro without insurance
Their senior citizen discounts are much appreciated.
Their dedication to global health is evident.
https://cytotecpharm24.top/
Their global outlook is evident in their expansive services.
They’re globally renowned for their impeccable service.
gabapentin capsules usp 100mg
Always responsive, regardless of time zones.
Fast From India: Fast From India – Online medicine home delivery
india pharmacy mail order: top 10 pharmacies in india – Fast From India
https://fastfromindia.com/# indian pharmacy
п»їlegitimate online pharmacies india
Fast From India: Fast From India – buy medicines online in india
https://fastfromindia.com/# mail order pharmacy india
buy medicines online in india
Fast From India: Fast From India – top online pharmacy india
pharmacy website india indianpharmacy com mail order pharmacy india
indian pharmacy online
http://fastfromindia.com/# pharmacy website india
Online medicine order
pharmacy website india: indian pharmacy paypal – Fast From India
Fast From India: reputable indian pharmacies – Fast From India
https://fastfromindia.com/# Fast From India
Fast From India
Fast From India: Fast From India – world pharmacy india
Fast From India india pharmacy Fast From India
best india pharmacy
https://fastfromindia.shop/# Fast From India
Fast From India
Fast From India: Fast From India – indianpharmacy com
indianpharmacy com: Fast From India – Fast From India
http://pharmainternationale.com/# pharmacies en ligne certifiГ©es
pharmacie en ligne livraison europe
trouver un mГ©dicament en pharmacie п»їpharmacie en ligne france Pharma Internationale
Achat mГ©dicament en ligne fiable: Pharma Internationale – Pharma Internationale
https://pharmainternationale.shop/# Pharma Internationale
pharmacie en ligne france fiable
acheter mГ©dicament en ligne sans ordonnance: Pharma Internationale – pharmacie en ligne sans ordonnance
Pharma Internationale: Pharma Internationale – pharmacie en ligne france pas cher
Pharma Internationale pharmacie en ligne fiable п»їpharmacie en ligne france
pharmacie en ligne sans ordonnance: pharmacies en ligne certifiГ©es – п»їpharmacie en ligne france
pharmacie en ligne pas cher: Achat mГ©dicament en ligne fiable – pharmacie en ligne france livraison internationale
http://pharmainternationale.com/# pharmacie en ligne france livraison internationale
Pharma Internationale
acheter mГ©dicament en ligne sans ordonnance: pharmacie en ligne – Pharma Internationale
Pharmacie en ligne livraison Europe: Pharmacie sans ordonnance – Pharma Internationale
vente de mГ©dicament en ligne: vente de mГ©dicament en ligne – pharmacie en ligne sans ordonnance
Pharma Internationale: pharmacie en ligne france pas cher – Pharma Internationale
https://farmaciamedic.com/# farmacias online seguras
п»їfarmacia online espaГ±a
farmacias direct: farmacia online 24 horas – farmacia online envГo gratis
Farmacia Medic: п»їfarmacia online espaГ±a – Farmacia Medic
Farmacia Medic: farmacia online envГo gratis – farmacia online barata
farmacias online seguras en espaГ±a: Farmacia Medic – farmacia online envГo gratis
farmacia online 24 horas: farmacia barata – Farmacia Medic
Farmacia Medic Farmacia Medic farmacia online envГo gratis
farmacias online seguras en espaГ±a: farmacia online 24 horas – farmacia online barcelona
http://topmaxfarma.com/# Top Max Farma
Top Max Farma
Top Max Farma: acquistare farmaci senza ricetta – comprare farmaci online con ricetta
migliori farmacie online 2024: Top Max Farma – Top Max Farma
Top Max Farma Farmacie on line spedizione gratuita Top Max Farma
comprare farmaci online all’estero: farmacia online senza ricetta – Top Max Farma
Top Max Farma: Top Max Farma – Top Max Farma
Farmacia online piГ№ conveniente: Farmacie on line spedizione gratuita – Top Max Farma
Top Max Farma: Top Max Farma – farmacia online
http://topmaxfarma.com/# top farmacia online
migliori farmacie online 2024
farmaci senza ricetta elenco: Top Max Farma – Top Max Farma
comprare farmaci online all’estero: farmacie online autorizzate elenco – top farmacia online
https://topmaxfarma.com/# Top Max Farma
Farmacia online piГ№ conveniente
Top Max Farma comprare farmaci online all’estero Top Max Farma
IndianPharmacyAbp: indian pharmacy – Online medicine home delivery
https://indianpharmacyabp.com/# Best Indian pharmacy
best online pharmacies in mexico
http://canadianpharmacyaapd.com/# pharmacy canadian superstore
Online medicine order
mexican pharmacy acp: mexican pharmacy acp – mexican pharmacy acp
https://mexicanpharmacyacp.com/# mexican pharmacy acp
reputable indian online pharmacy
india pharmacy mail order IndianPharmacyAbp Indian pharmacy international shipping
mexico drug stores pharmacies: mexican pharmacy acp – п»їbest mexican online pharmacies
http://indianpharmacyabp.com/# Indian pharmacy international shipping
mexico drug stores pharmacies
canadian pharmacy uk delivery: canadian pharmacy ratings – canadian pharmacy india
mexican pharmacy acp: mexican pharmacy acp – mexican pharmacy acp
https://indianpharmacyabp.shop/# cheapest online pharmacy india
mexico pharmacies prescription drugs
canadian pharmacy tampa: canadian drugs online – canadian pharmacy sarasota
http://mexicanpharmacyacp.com/# mexican pharmacy acp
mexican pharmaceuticals online
IndianPharmacyAbp top 10 online pharmacy in india Indian pharmacy international shipping
https://canadianpharmacyaapd.shop/# prescription drugs canada buy online
mexico drug stores pharmacies
Indian Pharmacy Abp: Indian pharmacy international shipping – Best online Indian pharmacy
Indian Pharmacy Abp: Indian Pharmacy Abp – Online medicine home delivery
mexican pharmacy acp: mexico pharmacies prescription drugs – medicine in mexico pharmacies
legitimate canadian pharmacies: Canadian Pharmacy AAPD – my canadian pharmacy review
Best online Indian pharmacy cheapest online pharmacy india Indian pharmacy international shipping
Online medicine home delivery: Best online Indian pharmacy – India pharmacy ship to USA
canadian discount pharmacy: Canadian Pharmacy AAPD – online canadian drugstore
Indian pharmacy international shipping: Best Indian pharmacy – Indian pharmacy international shipping
pharmacies in mexico that ship to usa: purple pharmacy mexico price list – mexican online pharmacies prescription drugs
India pharmacy ship to USA: Online medicine home delivery – Indian pharmacy online
indian pharmacy indian pharmacy India pharmacy ship to USA
canada drugs online: best mail order pharmacy canada – legit canadian pharmacy
http://mexicanpharmacyacp.com/# mexico pharmacies prescription drugs
mexico pharmacies prescription drugs
Online medicine home delivery: Indian Pharmacy Abp – India pharmacy ship to USA
balloon игра на деньги balloon игра на деньги Казино предлагает отличные условия для РёРіСЂС‹.
Баллон — это автомат для настоящих любителей.: balloon game – balloon казино
https://neokomsomol.kz/# Выигрывайте большие суммы на автоматах!
Крути барабаны Рё жди победы!: balloon game – balloon игра
Рграйте РїРѕ СЃРІРѕРёРј правилам РЅР° автомате.: balloon казино официальный сайт – balloon казино играть
https://neokomsomol.kz/# Казино — место для увлекательных игр.
Ballon — это ваш шанс РЅР° победу.: balloon казино демо – balloon game
Ballon — РёРіСЂР°, полная СЃСЋСЂРїСЂРёР·РѕРІ.: balloon игра – balloon казино официальный сайт
https://balloonigra.kz/# Казино предлагает отличные условия для игры.
https://akhbutina.kz/# Ballon — это игра с удивительными графиками.
Рграйте РІ казино, наслаждайтесь каждым моментом.: balloon казино демо – balloon game
Выигрывайте большие СЃСѓРјРјС‹ РЅР° автоматах!: balloon казино демо – balloon казино
Ставь РЅР° деньги Рё выигрывай легко!: balloon казино – balloon казино официальный сайт
balloon игра balloon казино демо Найдите СЃРІРѕР№ lucky slot РІ казино.
Каждый СЃРїРёРЅ может стать выигрышным!: balloon game – balloon игра на деньги
Казино — РјРёСЂ азартных приключений.: balloon игра на деньги – balloon казино демо
https://balloonigra.kz/# Найдите свой lucky slot в казино.
Баллон — это автомат для настоящих любителей.: balloon игра – balloon игра
balloon казино играть balloon игра на деньги п»їРРіСЂРѕРІРѕР№ автомат Ballon дарит СЏСЂРєРёРµ эмоции.
Динамичная РёРіСЂР° РЅР° автомате Ballon ждет вас.: balloon казино демо – balloon казино официальный сайт
https://balloonigra.kz/# Погрузитесь в мир азартных игр.
https://alo789.auction/# dang nh?p alo789
k8 bet nha cai k8 k8 bet
alo789in: alo789hk – alo789in
789alo: alo789 chinh th?c – alo 789
https://88betviet.pro/# nha cai 88bet
http://alo789.auction/# alo 789
https://alo789.auction/# alo789hk
k8 th? dam: link vao k8 – k8 bet
88 bet 88bet 88bet slot
http://k8viet.guru/# link vao k8
https://alo789.auction/# dang nh?p alo789
https://k8viet.guru/# k8vip
alo789 dang nh?p: dang nh?p alo789 – alo789hk
http://k8viet.guru/# link vao k8
nha cai k8: k8vip – nha cai k8
alo 789 dang nh?p alo789 dang nh?p 789alo
http://alo789.auction/# alo789in
alo 789 789alo alo789 chinh th?c
alo789 chinh th?c: 789alo – alo 789
https://k8viet.guru/# k8 th? dam
88 bet keo nha cai 88bet 188bet 88bet
https://k8viet.guru/# k8 th? dam
https://interpharmonline.com/# reputable canadian online pharmacy
canadian drug stores
https://indiamedfast.shop/# india pharmacy without prescription
vipps approved canadian online pharmacy
https://indiamedfast.shop/# buying prescription drugs from india
mexican pharmacy online order: Mexican Pharm International – reliable mexican pharmacies
https://indiamedfast.com/# India Med Fast
mexican pharmacy online store Mexican Pharm International reliable mexican pharmacies
canadian pharmacy online ship to usa: online canadian pharmacy no prescription – northwest canadian pharmacy
http://interpharmonline.com/# trusted canadian pharmacy
canadian online drugstore
mexican pharmacy online store: mexican pharmacy online store – mexican pharmacy online store
https://mexicanpharminter.shop/# reliable mexican pharmacies
canada drugs reviews
canadian pharmacy online reviews: fda approved canadian online pharmacies – safe reliable canadian pharmacy
http://interpharmonline.com/# buy prescription drugs from canada cheap
legit canadian online pharmacy
reputable canadian pharmacy: highest rated canadian online pharmacy – canadian pharmacies
https://mexicanpharminter.shop/# reliable mexican pharmacies
canada pharmacy world
india online pharmacy store: cheapest online pharmacy india – online medicine shopping in india
canadian online pharmacy: canadian drugstore online no prescription – precription drugs from canada
https://interpharmonline.shop/# best online canadian pharmacy
online canadian drugstore
https://generic100mgeasy.com/# buy generic 100mg viagra online
kamagra gel kopen: kamagra 100mg kopen – kamagra jelly kopen
KamagraKopen.pro: Kamagra Kopen Online – Officiele Kamagra van Nederland
cialis without a doctor prescription: Buy Cialis online – TadalafilEasyBuy.com
http://tadalafileasybuy.com/# Tadalafil Easy Buy
Tadalafil Easy Buy: TadalafilEasyBuy.com – Tadalafil Easy Buy
https://tadalafileasybuy.shop/# Cialis over the counter
https://generic100mgeasy.shop/# Generic 100mg Easy
http://tadalafileasybuy.com/# cialis without a doctor prescription
Generic100mgEasy: Generic 100mg Easy – Generic 100mg Easy
Generic100mgEasy: best price for viagra 100mg – Generic100mgEasy
Generic100mgEasy: Generic 100mg Easy – Generic100mgEasy
https://kamagrakopen.pro/# Kamagra Kopen
kamagra jelly kopen: Kamagra Kopen – kamagra kopen nederland
TadalafilEasyBuy.com: Buy Tadalafil 20mg – Buy Tadalafil 10mg
Officiele Kamagra van Nederland: Kamagra – kamagra kopen nederland
KamagraKopen.pro: kamagra kopen nederland – Officiele Kamagra van Nederland
kamagra gel kopen: Kamagra Kopen Online – kamagra jelly kopen
https://generic100mgeasy.com/# buy generic 100mg viagra online
kamagra pillen kopen: KamagraKopen.pro – KamagraKopen.pro
http://tadalafileasybuy.com/# TadalafilEasyBuy.com
kamagra 100mg kopen: KamagraKopen.pro – Kamagra
пин ап: https://pinupkz.life/
пин ап зеркало – пин ап казино зеркало
pinup 2025 – пин ап казино официальный сайт
Generic 100mg Easy buy generic 100mg viagra online Generic100mgEasy
пин ап казино официальный сайт – пин ап
пин ап казино официальный сайт – пин ап казино зеркало
пин ап казино: https://pinupkz.life/
KamagraKopen.pro kamagra 100mg kopen Kamagra Kopen
пин ап казино зеркало – pinup 2025
Apotheek online bestellen: Betrouwbare online apotheek zonder recept – Apotheek Max
Apoteket online: Apoteket online – Apotek hemleverans idag
Kamagra Gel: Kamagra kaufen – Kamagra Oral Jelly
https://apotekonlinerecept.shop/# apotek pa nett
http://apotheekmax.com/# Online apotheek Nederland zonder recept
https://apotekonlinerecept.com/# Apotek hemleverans idag
https://apotekonlinerecept.com/# Apoteket online
Kamagra kaufen Kamagra Gel Kamagra online bestellen
Apotek hemleverans idag: Apotek hemleverans idag – Apoteket online
https://apotekonlinerecept.com/# Apoteket online
Online apotheek Nederland met recept: de online drogist kortingscode – Online apotheek Nederland met recept
apotek online recept apotek pa nett apotek pa nett
Apoteket online: Apoteket online – Apotek hemleverans recept
online apotheek: Online apotheek Nederland met recept – Apotheek Max
Online apotheek Nederland zonder recept: Betrouwbare online apotheek zonder recept – Apotheek online bestellen
Online apotheek Nederland met recept: Betrouwbare online apotheek zonder recept – online apotheek
Apotek hemleverans recept: Apotek hemleverans recept – Apotek hemleverans idag
Kamagra kaufen ohne Rezept kamagra kamagra
http://apotekonlinerecept.com/# Apotek hemleverans recept
apotek pa nett: apotek pa nett – apotek online
http://apotheekmax.com/# online apotheek
https://apotekonlinerecept.com/# Apotek hemleverans idag
http://apotekonlinerecept.com/# Apotek hemleverans recept
apotek online recept apotek online apotek pa nett
http://kamagrapotenzmittel.com/# Kamagra kaufen
canadian family pharmacy: go canada pharm – canadian drug stores
top 10 online pharmacy in india: www india pharm – www india pharm
onlinecanadianpharmacy 24: canada drugs reviews – canadian pharmacy phone number
best online pharmacies in mexico: medicine in mexico pharmacies – Agb Mexico Pharm
canadian online pharmacy: GoCanadaPharm – legitimate canadian pharmacies
canadian pharmacy drugs online: canadian family pharmacy – ed drugs online from canada
https://agbmexicopharm.shop/# Agb Mexico Pharm
top 10 pharmacies in india: www india pharm – www india pharm
www india pharm: best india pharmacy – Online medicine order
https://wwwindiapharm.shop/# www india pharm
Agb Mexico Pharm mexican online pharmacies prescription drugs medication from mexico pharmacy
best online pharmacy india: indianpharmacy com – www india pharm
www india pharm: www india pharm – buy prescription drugs from india
mail order pharmacy india: www india pharm – www india pharm
http://agbmexicopharm.com/# Agb Mexico Pharm
buy medicines online in india: www india pharm – www india pharm
www india pharm: cheapest online pharmacy india – п»їlegitimate online pharmacies india
http://wwwindiapharm.com/# www india pharm
Agb Mexico Pharm: Agb Mexico Pharm – mexico pharmacies prescription drugs
Agb Mexico Pharm: reputable mexican pharmacies online – Agb Mexico Pharm
https://agbmexicopharm.com/# pharmacies in mexico that ship to usa
pharmacy canadian: canadapharmacyonline – canadian pharmacy mall
www india pharm: indian pharmacies safe – indian pharmacy
zithromax 1000 mg online: ZithPharmOnline – ZithPharmOnline
AmOnlinePharm: buy amoxicillin 500mg uk – where can you get amoxicillin
lisinopril 30: buy zestril online – zestril price in india
Pred Pharm Net Pred Pharm Net where can i get prednisone
Pred Pharm Net: average cost of prednisone 20 mg – buy prednisone without a prescription best price
ZithPharmOnline: ZithPharmOnline – ZithPharmOnline
Lisin Express: price of lisinopril in india – lisinopril 5 mg tablet
buying amoxicillin in mexico: where to buy amoxicillin 500mg without prescription – amoxicillin 250 mg capsule
Lisin Express: Lisin Express – Lisin Express
Clom Fast Pharm: Clom Fast Pharm – buying generic clomid no prescription
https://predpharmnet.com/# Pred Pharm Net
3000mg prednisone: canada buy prednisone online – Pred Pharm Net
where to get clomid without rx: can you get clomid without dr prescription – where to buy cheap clomid without insurance
ZithPharmOnline: buy zithromax 1000mg online – ZithPharmOnline
zithromax for sale online: ZithPharmOnline – ZithPharmOnline
lisinopril 10 mg best price: where to buy lisinopril without prescription – buy cheap lisinopril 40mg
zithromax for sale usa: ZithPharmOnline – purchase zithromax z-pak
https://clomfastpharm.shop/# where buy clomid prices
order clomid without a prescription: can i get generic clomid without prescription – clomid cost
lisinopril without an rx: Lisin Express – lisinopril online without prescription
Clom Fast Pharm Clom Fast Pharm Clom Fast Pharm
lisinopril pills for sale: Lisin Express – Lisin Express
AmOnlinePharm: AmOnlinePharm – AmOnlinePharm
generic for prinivil: prescription drug lisinopril – Lisin Express
Lisin Express: buy cheap lisinopril – Lisin Express
http://casinositeleri1st.com/# guvenilir casino siteleri
canlД± bahis oyunlarД±: casibom giris – vidobet casibom1st.com
casino siteleri: casino siteleri 2025 – casino siteleri casinositeleri1st.com
sweet bonanza slot: sweet bonanza yorumlar – sweet bonanza demo sweetbonanza1st.shop
deneme bonusu veren siteler: como bakery yorumlarД± – deneme bonusu veren siteler casinositeleri1st.com
casino siteleri: deneme bonusu veren siteler – lisansl? casino siteleri casinositeleri1st.com
bГјtГјn oyun siteleri: casibom giris – bonus veren idda siteleri casibom1st.com
sweet bonanza demo: sweet bonanza oyna – sweet bonanza oyna sweetbonanza1st.shop
sweet bonanza sweet bonanza yorumlar sweet bonanza sweetbonanza1st.com
sweet bonanza yorumlar: sweet bonanza giris – sweet bonanza 1st sweetbonanza1st.shop
en iyi casino sitesi: casibom giris – casinoda en Г§ok kazandД±ran oyun casibom1st.com
gГјvenilir bahis siteleri casibom guncel giris casino slot oyunlarД± casibom1st.shop
gГјvenilir oyun alma siteleri: internet kumar oyunu – deneme bonusu veren siteler casinositeleri1st.com
casino siteleri: slot casino siteleri – en iyi bahis siteleri 2024 casinositeleri1st.com
sweet bonanza siteleri: sweet bonanza yorumlar – sweet bonanza 1st sweetbonanza1st.shop
canlД± casino bonusu veren siteler en iyi yasal bahis siteleri deneme bonusu veren siteler casinositeleri1st.shop
sweet bonanza slot: sweet bonanza siteleri – sweet bonanza 1st sweetbonanza1st.shop
sweet bonanza yorumlar: sweet bonanza siteleri – sweet bonanza demo sweetbonanza1st.shop
casino siteleri 2025 slot casino siteleri deneme bonusu veren siteler casinositeleri1st.shop
slot casino siteleri: casino siteleri – slot casino siteleri casinositeleri1st.com
lisansl? casino siteleri en gГјvenilir bahis siteleri 30 tl bonus veren bahis siteleri casinositeleri1st.shop
certified Mexican pharmacy: Mexican pharmacy ship to USA – USMexPharm
UsMex Pharm: Mexican pharmacy ship to USA – Us Mex Pharm
mexican pharmacy: certified Mexican pharmacy – mexico drug stores pharmacies
Mexican pharmacy ship to USA: USMexPharm – Us Mex Pharm
UsMex Pharm: usa mexico pharmacy – mexican pharmacy
USMexPharm certified Mexican pharmacy USMexPharm
usa mexico pharmacy: UsMex Pharm – USMexPharm
http://usmexpharm.com/# pharmacies in mexico that ship to usa
USMexPharm: USMexPharm – Us Mex Pharm
Us Mex Pharm: Mexican pharmacy ship to USA – USMexPharm
certified Mexican pharmacy: USMexPharm – UsMex Pharm
http://usmexpharm.com/# Mexican pharmacy ship to USA
UsMex Pharm: mexican pharmacy – certified Mexican pharmacy
certified Mexican pharmacy: mexican pharmacy – usa mexico pharmacy
buy prescription drugs from india: USA India Pharm – UsaIndiaPharm
UsaIndiaPharm: UsaIndiaPharm – USA India Pharm
indian pharmacy paypal: UsaIndiaPharm – USA India Pharm
https://usaindiapharm.shop/# online shopping pharmacy india
UsaIndiaPharm: USA India Pharm – USA India Pharm
UsaIndiaPharm: USA India Pharm – indian pharmacy paypal
https://usaindiapharm.shop/# indian pharmacy paypal
indian pharmacy п»їlegitimate online pharmacies india UsaIndiaPharm
http://usaindiapharm.com/# USA India Pharm
https://usaindiapharm.shop/# USA India Pharm
UsaIndiaPharm USA India Pharm indian pharmacy online
USA India Pharm: USA India Pharm – online pharmacy india
india pharmacy mail order: USA India Pharm – USA India Pharm
http://usaindiapharm.com/# UsaIndiaPharm
india online pharmacy: top 10 pharmacies in india – UsaIndiaPharm
indianpharmacy com: Online medicine order – Online medicine order
USA India Pharm: USA India Pharm – india pharmacy mail order
USA India Pharm: UsaIndiaPharm – world pharmacy india
UsaIndiaPharm: USA India Pharm – top 10 online pharmacy in india
Online medicine order: UsaIndiaPharm – india pharmacy mail order
best india pharmacy: UsaIndiaPharm – Online medicine home delivery
india pharmacy: UsaIndiaPharm – indian pharmacy online
USA India Pharm: mail order pharmacy india – USA India Pharm
https://usaindiapharm.com/# USA India Pharm
indian pharmacy paypal UsaIndiaPharm USA India Pharm
best india pharmacy: mail order pharmacy india – india pharmacy mail order
UsaIndiaPharm: Online medicine order – india pharmacy
https://usaindiapharm.com/# USA India Pharm
п»їlegitimate online pharmacies india: cheapest online pharmacy india – UsaIndiaPharm
USA India Pharm: USA India Pharm – UsaIndiaPharm
UsaIndiaPharm: UsaIndiaPharm – USA India Pharm
canadian pharmacy: USACanadaPharm – canada drugs online
http://usacanadapharm.com/# canada pharmacy world
my canadian pharmacy: canadian 24 hour pharmacy – pharmacies in canada that ship to the us
usa canada pharm: pet meds without vet prescription canada – canadian compounding pharmacy
buy canadian drugs usa canada pharm USACanadaPharm
USACanadaPharm: best canadian pharmacy online – USACanadaPharm
usa canada pharm: USACanadaPharm – USACanadaPharm
canadian pharmacy 24h com safe: canada pharmacy world – USACanadaPharm
canadian pharmacy no scripts: usa canada pharm – USACanadaPharm
USACanadaPharm: usa canada pharm – canadian pharmacy no scripts
usa canada pharm: USACanadaPharm – USACanadaPharm
canada pharmacy online: USACanadaPharm – canadian discount pharmacy
USACanadaPharm usa canada pharm canadian pharmacy online
http://usacanadapharm.com/# USACanadaPharm
usa canada pharm: USACanadaPharm – escrow pharmacy canada
usa canada pharm: buying from canadian pharmacies – usa canada pharm
usa canada pharm canadian neighbor pharmacy rate canadian pharmacies
USACanadaPharm: canadian pharmacy phone number – USACanadaPharm
usa canada pharm: canadian online pharmacy – best canadian pharmacy online