Code Signing Certificate – Different Types, How they Work and How they are Different
The use of technology has made our lives easier, and we can have everything at our fingertips. However, the use of technology has also led to the growth of cybercrimes.
And not only websites but even mobile apps are also being used by hackers to lay their hands on your sensitive information. There are several unsafe ways on the internet and mobile app stores to always be on your guard.
Studies show that cybercrime could lead to a cost of US$ 6 trillion globally by 2021. A study by Appsflyer shows that an analysis of 2.5 billion installations of 9500 apps has shown an increase in app install fraud rates.
While an SSL certificate is used to protect your website and networks, it is also necessary to protect your software. Businesses have been installing a code signing certificate to prevent unauthorised changes to the underlying code.
- Understanding a Code Signing Certificate
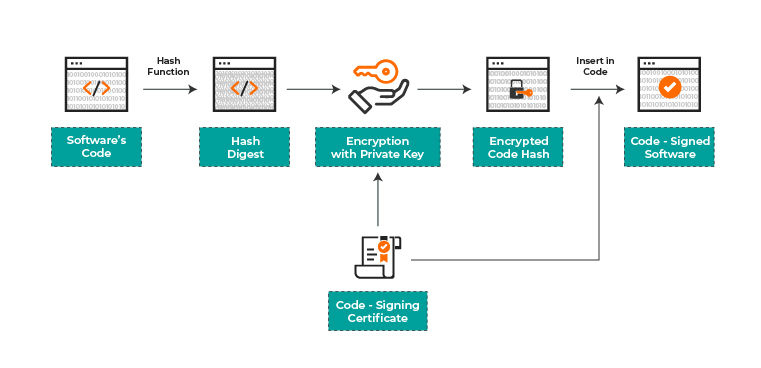
Software developers use the code signing certificate to sign the software programs, executables and drivers digitally. It also contains data that can identify the developer of the software entirely.
The technology involves using a private and public key pair – or the Public Key Infrastructure (PKI). The developer signs the code with the private key, while the user uses the public key to ensure the developer’s authenticity
.
(Source: https://www.appviewx.com/education-center/what-is-code-signing)
Before downloading the software, you must verify the developer’s identity and ensure it has not been damaged. This certificate uses a digital signature, and a timestamp is recorded when it is applied.
This feature ensures that the underlying code remains valid even after the expiry of the digital certificate. Only if you have to make changes to the code you must digitally sign it again.
- Understanding the requirement for Code Signing Certificate
There has been an increase in the number of incidents where fraudulent software has been downloaded. A code signing certificate helps validate the software developer and prevents any malicious attempt to tamper with your software.
Identifies the software source.
The certificate will help the user to confirm the source of the software. It is also necessary for the developer to sign the code using the certificate. If the code is not signed, a warning message will be displayed showing that the publisher is unknown.
Confirms software integrity.
The use of a code signing certificate ensures that the integrity of the software is intact. The code is not altered towards any malicious end and helps enthuse trust in the users trying to download the software. Developers can also use their brand name and prevent any unwanted alterations to the software.
Meets requirements of platforms.
The platforms expect that you will consider the safety of your customer data. For this reason, the users get a pop-up alerting them if the software is not digitally signed. Signing the code can also help to detect any modified files. It also ensures a smoother download process of the software.
- Understanding the workings of a Code Signing certificate
First, you must apply for the certificate at the Certificate Authority (CA) of your choice. The installation procedure may vary across the different CAs. Generally, a one-way hash is developed of the software, and a private key is used to encrypt the hash. The digital signature is also added to the code using the private key.
The hash functions are designed such that they are irreversible. When any user wants to download the software, the certificate’s authenticity is checked and confirmed by a trusted CA. The user’s system then uses the public key to decrypt the signature. The system will then look for a root certificate that trusts the signature. If the trustworthy root certificate cannot be found, the system will tell the user that the certificate used to sign the software cannot be trusted.
The software is hashed again, and the new value is compared with the hash used to sign the application. When the system trusts the root certificate and the hashes also match, the user can safely download the software.
- An Insight into the Kinds of Code Signing certificates
There are two types of code signing certificates, viz.
1. Organisation Validated Code Signing (Also referred to as regular Code Signing)
2. Extended Validated (EV) Code Signing
- Understanding EV Code Signing
An EV code signing certificate involves the CA undertaking a rigorous background check of the organisation that wishes to procure this certificate. There is various documentation that the entity must produce. The entity must be registered officially with the government and must be operating then.
The EV code signing certificate has an intelligent security system known to be trusted by the Microsoft SmartScreen filter. The users have ready protection against any phishing techniques and request malware downloads. These certificates are best for device drivers, applications and executables.
As an additional precaution, the private key is mailed physically to the entity requested for this certificate. It must be stored safely so that only the authorised personnel can gain access.
- How does EV Code signing work?
After the software code has been completed, it is hashed and cannot be easily altered. The private key stored in the external hardware is used to sign the software digitally and provide a timestamp. It will help the web browsers to know about the software developer and whether the certificate can be trusted.
When the software has been signed, it can be made available for downloading. Once a user tries to download the software, the browser can understand who the software developer is and whether any unauthorised changes were made.

(Source: https://www.ssl2buy.com/wiki/regular-code-signing-vs-ev-code-signing)
- Difference between EV Code Signing and Regular Code Signing
We will now have a look at the differences between these two options.
| EV Code Signing Certificate | Regular Code Signing Certificate |
| The private key is stored as a hardware token. However, you must keep it safe. | Protecting the private key is the prerogative of the developers. It increases the risk of it being misused. |
| It automatically receives the Microsoft SmartScreen Recognition. It provides additional trust for the software. | The reputation is built as users continue to install the software. |
| CAs use an elaborate process to validate the developer credentials. | The CAs have a straightforward process to validate the credentials of the business. |
| The CAs must follow the CA/Browser forum guidelines to vet the business. | No such guidelines need to be followed. |
| CAs can take up to five days to issue this certificate. | The certificate can be received within three days. |
| These certificates are offered at a premium. However, there are better security features. | It is available at a lower price. |
Conclusion
Users download software to make their lives easier. It is necessary to assess whether the software is genuine so that users do not fall prey to hackers. Businesses must ensure that the users can download the software without worrying about the software being altered midway. It becomes necessary to safeguard software downloads like websites that are kept secure using an SSL certificate.
The use of a code signing certificate can ensure that users can download the software without fear. Without the certificate, the software can be marked as unsafe for downloads and cause revenue loss. Again, you can use the EV code signing certificate that automatically receives Microsoft SmartScreen Recognition. The use of an external drive to store the private key is another advantage.